DoD 5200.39-R
DEPARTMENT OF
DEFENSE

MANDATORY PROCEDURES FOR RESEARCH AND TECHNOLOGY PROTECTION WITHIN THE DOD
-
Draft -
MARCH 2002
ASSISTANT SECRETARY OF DEFENSE
FOR
COMMAND, CONTROL, COMMUNICATIONS, AND INTELLIGENCE
ASD (C3I)
Draft - December 20, 2001
March 2002
FOREWORD
This Regulation is issued under the authority of Department of Defense (DoD) Directive 5200.39, �Research and Technology Protection (RTP) within the Department of Defense� (reference (a)) and is effective immediately.� This Regulation establishes mandatory procedures for protecting specified critical research technology (CRT) and critical program information (CPI) throughout the DoD as well as for dual-use and leading edge military technology being developed under the auspices of the DoD.� In some cases, RTP may begin at a DoD Research, Development, Test and Evaluation (RDT&E) facility and extend into and throughout the life cycle of the acquisition effort, deployment, and use until demilitarization.
Application of procedures to protect research and technology as described within this Regulation achieves several goals:
-���� Provides increased leverage for an effective and informative measured sharing of intelligence and defense systems/technology with foreign countries during negotiations to obtain base rights agreements for a U.S. response to terrorist actions.�
-���� Allows sharing developmental costs and production investments with other countries�yet protects U.S. end-items throughout their life cycle by incorporating system security engineering (SSE) and anti-tamper (AT) techniques.�
-���� Maintains U.S. dual-use and leading-edge military technology superiority.�
-���� Optimizes capital investments in the U.S. military / U.S. industrial complex.�
-���� Increases U.S. and corporate strength during routine business negotiations abroad.�
-���� Leverages U.S. advantage during treaty negotiations (i.e., anti- or counter-terrorism).
-���� Avoids lead-time for research, and the need for additional RDT&E appropriations, to replace compromised technology.�
-���� Establishes the U.S. warfighter advantage for success, superiority, and safety in the battlespace and during exigent coalition operations.�
This Regulation applies to the Office of the Secretary of Defense, the Military Departments , the Chairman of the Joint Chiefs of Staff, the Combatant Commands, the Inspector General of the Department of Defense, the Defense Agencies, and DoD Field Activities (hereafter referred to collectively as �the DoD Components�).
This Regulation is for use by all DoD Components.� The Heads of DoD Components should issue supplementary instructions, when necessary, and provide examples of their plans or implementation procedures.� These supplementary instructions and examples should be included in the Defense Acquisition Deskbook (DAD)and the Specialized C3I Operating Reference (SCOR).
The Defense RTP Council (DRTPC) shall receive and consider proposals for, and, as necessary, generate changes to this Regulation.� The DRTPC shall submit proposed changes to the Assistant Secretary of Defense (Command, Control, Communications, and Intelligence) (ASD(C3I)); the Under Secretary of Defense (Acquisition, Technology, and Logistics) (USD(AT&L)); and, the Director of Operational Test and Evaluation (DOT&E), who have sole authority to change this Regulation.� All three officials shall jointly sign changes.� The Director of Security, Office of the Deputy Assistance Secretary of Defense (Security and Information Operations) (ODASD(S&IO))/OASD(C3I), shall maintain administrative control of this Regulation and shall publish all signed changes.
Send recommended changes to this Regulation to:
�������������� Deputy Director for Research and Technology Protection
�������������� Security Directorate
�������������� Office of the Assistant Secretary of Defense for Command, Control, Communications and Intelligence, ASD(C3I)
�������������� 6000 Defense Pentagon
�������������� Washington, DC�� 20301-6000
__________________�������������������� ________________����������������������������� ____________
E.
C. Aldridge Jr.������������������������������ John
P. Stenbit �������������������������������������� Thomas
P. Christie
Under Secretary�������������������������������� Assistant Secretary�������������������������������� Director of
of Defense ��������������������������������������� of
Defense ������������������������������������������� Operational
Test
(Acquisition, Technology,������������������� (Command, Control, ������������������������������ and Evaluation
& Logistics)�������������������������������������� Communications,
and Intelligence)
TABLE OF CONTENTS
����������������������������������������������������������������������������������������������������������������������������������� �������� Page
Foreword������������������������������������������������������������������������������������������������������������������������������� 1
Table of Contents�������������������������������������������������������������������������������������������������������������������� 3
References��� �������������������������������������������������������������������������������������������������������������������������� 9
DL1.� Definitions 11
AL1.� Abbreviations and Acronyms��������������������������������������������������������������������������������������� 17
PART I� -� GENERAL
C1.� CHAPTER 1 - GENERAL INFORMATION�������������������������������������������������������������� 23
������ C1.1.� Purpose����������������������������������������������������������������������������������������������������������� 23
������ C1.2.� General������������������������������������������������������������������������������������������������������������ 23
������ C1.3.� Application������������������������������������������������������������������������������������������������������ 24
������ C1.4.� Defense Research and Technology Protection Council�������������������������������������� 25
������ C1.5.� RTP Protection Planning���������������������������������������������������������������������������������� 25
������ C1.6.� Marking, Dissemination, and Destruction of CRT and CPI�������������������������������� 26
������ C1.7.� Overview � Protection of CRT at RDT&E Activities���������������������������������������� 29
������ C1.8.� Overview � Protection of CPI in Acquisition����������������������������������������������������� 29
������ C1.9.� Overview - Security Support Plan (SSP)���������������������������������������������������������� 31
������ C1.10.� Overview - Counterintelligence Support Plan (CISP)�������������������������������������� 31
������ C1.11.� Anti-Tamper�������������������������������������������������������������������������������������������������� 31
������ C1.12.� Defense Acquisition Deskbook (DAD)����������������������������������������������������������� 31
������ C1.13.� Specialized C3I Operating Reference (SCOR)����������������������������������������������� 32
������ C1.14.� Economic Espionage�������������������������������������������������������������������������������������� 32
������ C1.15.� Information Reporting Requirements��������������������������������������������������������������� 33
������ C1.16.� Technology Protection Resource Directory����������������������������������������������������� 33
������ C1.17.� Regulation Overview�������������������������������������������������������������������������������������� 33
PART II - PROTECTION OF RESEARCH
TECHNOLOGY AT RDT&E ACTIVITIES
C2.� CHAPTER 2 - RDT&E ACTIVITY PROTECTION STRATEGY������������������������������� 37
������ C2.1.� General������������������������������������������������������������������������������������������������������������ 37
������ C2.2.� Protection Approaches������������������������������������������������������������������������������������ 37
C3.� CHAPTER 3 - PROTECTION PLANNING FOR RDT&E ACTIVITIES������������������� 39
������ C3.1.� General������������������������������������������������������������������������������������������������������������ 39
������ C3.2.� Identification of Critical Research Technology (CRT)���������������������������������������� 39
������ C3.3.� Protection Training and Awareness������������������������������������������������������������������� 39
������ C3.4.� Application of Safeguards�������������������������������������������������������������������������������� 39
������ C3.5.� Security Support Plan�������������������������������������������������������������������������������������� 42
������ C3.6.� Counterintelligence (CI) Support Plan��������������������������������������������������������������� 42
������ C3.7.� Information Assurance������������������������������������������������������������������������������������� 42
C4.� CHAPTER 4 - COUNTERINTELLIGENCE SUPPORT TO RDT&E ACTIVITIES
������ C4.1.� CI Support at DoD RDT&E Activities������������������������������������������������������������� 43
PART III - PROTECTION OF CPI IN ACQUISITION
PROGRAMS
C5.� CHAPTER 5 - PROGRAM PROTECTION STRATEGY������������������������������������������� 45
������ C5.1.� General������������������������������������������������������������������������������������������������������������ 47
������ C5.2.� Program Protection Strategy���������������������������������������������������������������������������� 47
C6.� CHAPTER 6 - PROGRAM PROTECTION PLANNING������������������������������������������� 49
������ C6.1.� General������������������������������������������������������������������������������������������������������������ 49
������ C6.2.� Critical Program Information (CPI)������������������������������������������������������������������� 50
������ C6.3.� Coordination���������������������������������������������������������������������������������������������������� 52
������ C6.4.� Program Protection Plan (PPP)������������������������������������������������������������������������ 53
������ C6.5.� System and Program Descriptions�������������������������������������������������������������������� 55
������ C6.6.� Foreign Collection Threat��������������������������������������������������������������������������������� 55
������ C6.7.� Vulnerabilities�������������������������������������������������������������������������������������������������� 56
������ C6.8.� RTP Countermeasures������������������������������������������������������������������������������������� 57
������ C6.9.� Security Classification Guides��������������������������������������������������������������������������� 59
������ C6.10.� Protection Costs�������������������������������������������������������������������������������������������� 59
C7.� CHAPTER 7 � MULTIDISCIPLINE CI THREAT ASSESSMENT���������������������������� 61
���������� C7.1.� General������������������������������������������������������������������������������������������������������������ 61
���������� C7.2.� Threat Analysis������������������������������������������������������������������������������������������������ 61
C8.� CHAPTER 8 - TECHNOLOGY ASSESSMENT/CONTROL PLAN (TA/CP)����������� 63
������ C8.1.� General������������������������������������������������������������������������������������������������������������ 63
������ C8.2.� Purpose����������������������������������������������������������������������������������������������������������� 63
���������� C8.3.� Content����������������������������������������������������������������������������������������������������������� 64
C9.� CHAPTER 9 - CONTRACTING AND RESOURCES������������������������������������������������ 67
���������� C9.1.� Early Coordination������������������������������������������������������������������������������������������� 67
���������� C9.2.� Pre-contract Award����������������������������������������������������������������������������������������� 67
���������� C9.3.� Post Contract Award��������������������������������������������������������������������������������������� 68
���������� C9.4.� Contractor Performance Monitoring����������������������������������������������������������������� 68
���������� C9.5.� Contractor Costs��������������������������������������������������������������������������������������������� 69
���������� C9.6.� Providing Documentation to Contractors���������������������������������������������������������� 69
���������� C9.7.� Support from Cognizant Government Industrial Security Offices������������������������ 69
C10.� CHAPTER 10 � RTP COSTING AND BUDGETING���������������������������������������������� 71
���������� C10.1.� General���������������������������������������������������������������������������������������������������������� 71
���������� C10.2.� RTP Costing�������������������������������������������������������������������������������������������������� 71
���������� C10.4.� RTP Budgeting���������������������������������������������������������������������������������������������� 71
C11.� CHAPTER 11 - EXECUTION OF THE PPP������������������������������������������������������������ 73
���������� C11.1.� General���������������������������������������������������������������������������������������������������������� 73
���������� C11.2.� Distribution of the PPP����������������������������������������������������������������������������������� 73
���������� C11.3.� Assessment of PPP Effectiveness������������������������������������������������������������������� 73
�������������������������������������������������������������������������������������������������������������������������������������������������
C12.� CHAPTER 12 � SYSTEMS SECURITY ENGINEERING���������������������������������������� 75
������ C12.1.� General���������������������������������������������������������������������������������������������������������� 75
������ C12.2.� Purpose��������������������������������������������������������������������������������������������������������� 75
������ C12.3.� System Security Engineering Planning������������������������������������������������������������� 75
������ C12.4.� System Security Engineering Process�������������������������������������������������������������� 76
������ C12.5.� Military Handbook 1785�������������������������������������������������������������������������������� 76
���������� C12.6.� Security Engineering for International Programs����������������������������������������������� 76
PART IV � PROTECTION ACTIVITIES
C13.� CHAPTER 13 - SECURITY SUPPORT PLAN��������������������������������������������������������� 79
���������� C13.1.� General���������������������������������������������������������������������������������������������������������� 79
���������� C13.2.� Purpose��������������������������������������������������������������������������������������������������������� 79
���������� C13.3.� Process��������������������������������������������������������������������������������������������������������� 79
C14.� CHAPTER 14 - COUNTERINTELLIGENCE SUPPORT PLAN����������������������������� 81
������ C14.1.� General���������������������������������������������������������������������������������������������������������� 81
������ C14.2.� CI Actions at RDT&E Activities��������������������������������������������������������������������� 81
������ C14.3.� CI Support Plan��������������������������������������������������������������������������������������������� 82
����������
C15.� CHAPTER 15 - ANTI-TAMPER TECHNIQUES����������������������������������������������������� 83
������ C15.1.� General���������������������������������������������������������������������������������������������������������� 83
������ C15.2.� Application of AT������������������������������������������������������������������������������������������ 83
������ C15.3.� AT Implementation���������������������������������������������������������������������������������������� 84
������ C15.4.� AT Verification and Validation����������������������������������������������������������������������� 85
������ C15.5.� Sustainment of AT����������������������������������������������������������������������������������������� 86
������ C15.6.� Guidelines for AT Disclosure�������������������������������������������������������������������������� 86
������ C15.7.� Review of AT������������������������������������������������������������������������������������������������ 87
C16.� CHAPTER 16 - HORIZONTAL ASSESSMENT AND PROTECTION������������������� 88
������ C16.1.� General���������������������������������������������������������������������������������������������������������� 88
������ C16.2.� Horizontal Assessments���������������������������������������������������������������������������������� 88
������ C16.3.� Horizontal Protection������������������������������������������������������������������������������������� 89
������ C16.4.� Reporting Requirements��������������������������������������������������������������������������������� 89
C17.� CHAPTER 17 - RTP ASSESSMENT AND INSPECTION�������������������������������������� 91
������ C17.1.� General���������������������������������������������������������������������������������������������������������� 91
������ C17.2.� Assessments�������������������������������������������������������������������������������������������������� 91
������ C17.3.� Inspections���������������������������������������������������������������������������������������������������� 91
C18.� CHAPTER 18 � INFORMATION ASSURANCE���������������������������������������������������� 93
������ C18.1.� General���������������������������������������������������������������������������������������������������������� 93
������ C18.2.� System Security Authorization Agreement������������������������������������������������������� 94
APPENDIX
���������� AP1.� Export Control Decision Guide ������������������������������������������������������������������������ 95
FIGURE
Figure��������������������������������������������������������������� Title����������������������������������������������������������� Page
�� C5.F1.� Acquisition Program Schedule������������������������������������������������������������������������������� 48
REFERENCES
� (a)���� DoD Directive 5200.39, �Research and Technology Protection within the Department of Defense,� March XX, 2002 (being prepared)
� (b)���� DoD Instruction 5000.2, �Operation of the Defense Acquisition System,� January 4, 2001, authorized by DoD Directive 5000.1, October 23, 2000
� (c)���� DoD 5200.1-R, �Information Security Program,� January 1997, authorized by DoD Directive 5200.1, December 13, 1996
� (d)���� DoD Directive 5240.2, �DoD Counterintelligence (CI),� May 22, 1997
� (e)���� 22CFR Part 120.11 of the International Traffic in Arms Regulations (ITAR)
�� (f)���� Section 2778 of title 22 United States Code, Arms Export Control Act
� (g)���� Executive Order 12958, �Classified National Security Information,� April 17, 1995, as amended
� (h)���� National
Security Decision Directives 189, �National Policy on
the Transfer of Scientific, Technical, and Engineering Information,� September
21, 1985
�� (i)���� Sections 271 et seq. of title 15, United States Code, �Computer Security Act of 1987�
�� (j)���� DoD Directive 2040.2, �International Transfers of Technology, Goods, Services, and Munitions,� January 17, 1984
� (k)���� DoD Directive 5230.11, �Disclosure of Classified Military Information to Foreign Governments and International Organizations,� June 16, 1992
�� (l)���� DoD Directive 5230.20, �Visits, Assignments, and Exchanges of Foreign Nationals,� August 12, 1998
(m)���� DoD Directive 5530.3, �International Agreements,� June 11, 1987
� (n)���� DoD Directive 5000.1, �The Defense Acquisition System, October 23, 2000
� (o)���� DoD 5000.2-R, �Mandatory Procedures for Major Defense Acquisition Programs (MDAPs) and Major Automated Information System (MAIS) Acquisition Programs,� January 4, 2001, authorized by DoD Directive 5000.1, October 23, 2000
� (p)���� DoD 5400.7-R, �DoD Freedom of Information Act Program,� September 1998, authorized by DoD Directive 5400.7, September 29, 1997
� (q)���� DoD Directive 5240.1, �DoD Intelligence Activities,� April 25, 1988
� (r)���� DoD 5240.1-R, �Procedures Governing the Activities of DoD Intelligence Components that Affect United States Persons,� December 1982, authorized by DoD Directive 5240.1, April 25, 1988
� (s)���� DoD Directive O-5205.7, �Special Access Program (SAP) Policy,� January 13, 1997
�� (t)���� DoD 5220.22-M, �National Industrial Security Program Operating Manual (NISPOM),� January 1995
� (u)���� Chapter 21 of title 44, United States Code, �National Archives And Records Administration�
� (v)���� Chapter 31 of title 44, United States Code, �Records Management by Federal Agencies�
(w)���� Chapter 33 of title 44, United States Code, �Disposal of Records�
� (x)���� DoD 7000.14-R, Volume IIB, Department of Defense Financial Management Regulation (Budget Presentation and Formulation), July 1998, authorized by DoD Instruction 7000.14, November 15, 1992
� (y)���� Chairman of the Joint Chiefs of Staff Instruction 3170.01B,
�Requirements Generation System,� April 15, 2001
� (z)���� Section 1831 et seq. of title 18, United States Code
(aa)���� DoD Instruction 5240.4, �Reporting of Counterintelligence and Criminal Violations,� September 22, 1992
(bb)��� DoD Directive 5200.1, �DoD Information Security Program,� December 13, 1996
(cc)���� DoD Directive 5230.24, �Distribution Statements on Technical Documents,� March 18, 1987
(dd)��� DoD Directive 5230.25, �Withholding of Unclassified Technical Data from Public Disclosure,� November 6, 1984
(ee)���� Export Administration Regulation (EAR), 50 U.S.C. app 2410
(ff)����� Militarily Critical Technologies List (MCTL), June 1996
(gg)���� National Disclosure Policy-1, �National Policy and Procedures for the Disclosure of Classified Military Information to Foreign Governments and International Organizations� (short title:� National Disclosure Policy (NDP-1)), October 1, 1988, as amended
(hh)���� Federal Information Processing Standard 140-2, �Security Requirements for Cryptographic Modules,� May 25, 2001
� (ii)���� DoD Directive 5200.27, �Acquisition of Information Concerning Persons and Organizations not Affiliated with the Department of Defense,� January 7, 1980
� (jj)���� Director of Central Intelligence Directive 1/7, �Security Controls on the Dissemination of Intelligence Information, (FOUO),�June 30, 1998
(kk)��� Director of Central Intelligence Directive 5/6, �Release of Intelligence and Intelligence-Related Information,� June 30, 1998
� (ll)���� National
Security Telecommunications and Information Systems Security Policy (NSTISSP)
number 8, �National Policy Governing the Release of INFOSEC Products or Associated
INFOSEC Information to Foreign Governments (U) (FOUO),� February 13, 1997
(mm)�� Section 2011 et seq. of title 42, United States Code, �Atomic Energy Act of August 30, 1954,� as amended
(nn)���� DoD Instruction S-5230.28, �Low Observable (LO) and Counter Low Observable (CLO) Programs (U),� May 12, 1997�
(oo)��� National Information Disclosure Policy Committee Policy Statement, �Foreign Release of Low Observable and Counter Low Observable Information and Capabilities (U),� PS-1/96, August 22, 1996 �����������
(pp)��� Defense Federal Acquisition Regulation (DFAR) Supplement, current edition
(qq)��� Military Handbook 1785, �System Security Engineering Program Management Requirements,� August 1, 1995
(rr)���� DoD O-5200.1-I, �Index of Security Classification Guides,� September 1996, authorized by DoD Directive 5200.1, December 13, 1996
(ss)���� OMB Circular A-130, �Management of Federal Information Resources,� February 1996
� (tt)���� DoD Global Information Grid Information Assurance Policy Memorandum No. 6-8510, June 16, 2001
(uu)���� DoD Instruction 5200.40, �DoD Information Technology Security Certification and Accreditation Process (DITSCAP), December 30, 1997
(vv)���� DoD 8510.1-M, �Department of Defense Information Technology Security Certification and Accreditation Process (DITSCAP) Application Manual,� July 2000
(ww)�� Section 1401 et seq. of title 40, United States Code, �Clinger-Cohen Act of 1996�
DL1.� DEFINITIONS
DL1.1.� The terms used in this Regulation are defined below:
DL1.1.1.� Acquisition Program.� A directed, funded effort designed to provide a new, improved, or continuing materiel, weapon, or information system or service capability in response to a validated operational or business need.� Acquisition programs are divided into different categories that are established to facilitate decentralized decision-making, execution, and compliance with statutory requirements.� Technology projects are not acquisition programs.� (DoD Instruction 5000.2, reference (b))
DL1.1.2.� Adversary.� A foreign interest (see DL1.1.15) or U.S. insider that conducts, or has the intent and/or capability to conduct, activities to collect Critical Research Technology and/or Critical Program Information.
DL1.1.3.� Anti-Tamper (AT).� The system engineering activities intended to prevent and/or delay exploitation of critical technologies in U.S. systems.� These activities involve the entire life cycle of systems acquisition, including research, design, development, testing, implementation, and validation of anti-tamper measures.� Properly employed, anti-tamper measures will add longevity to a critical technology by deterring efforts to reverse-engineer, exploit, or develop countermeasures against a system or system component.� (DoD Instruction 5000.2, reference (b))
DL1.1.4.� Automated Information
System (AIS).� An acquisition program that acquires
Information Technology (IT), except IT that:
DL1.1.4.1.� Involves equipment that is an integral part
of a weapon or weapons system; or
DL1.1.4.2.� Is a tactical communication system
(DoD Instruction 5000.2, reference (b)).�
DL1.1.5.� Compromise.� The unauthorized or inadvertent disclosure, destruction, transfer, alteration, or loss of critical research technology, critical program information, or classified information or material.�
DL1.1.6.� Controlled Unclassified Information.� Any information, the loss, misuse, or unauthorized access to which would or could adversely affect the organizational and/or national interest, but which does not meet classification criteria specified in DoD 5200.1-R (reference (c)).�
DL1.1.7.� Counterintelligence (CI).� Information gathered and activities conducted to protect against espionage, other intelligence activities, sabotage, or assassinations conducted by or on behalf of foreign governments or elements thereof, foreign organizations, or foreign persons, or international terrorist activities (DoD Directive 5240.2, reference (d)).
DL1.1.8.� Counterintelligence Support Plan (CISP).� A formally coordinated action plan that outlines CI support for protecting research and technology at specific DoD RDT&E facilities, DoD acquisition programs with critical program information, or organizations that fund work efforts external to DoD (e.g., Defense Advanced Research Projects Agency, Office of Naval Research, Air Force Office of Scientific Research).
DL1.1.9.� Critical Program Information (CPI).� Research, science, technology, or program information, technologies, processes, applications, or end items that, if compromised, would: degrade system combat effectiveness; compromise the program or system capabilities; shorten the expected combat-effective life of the system; significantly alter program direction; or, require additional research, development, test, and evaluation resources to counter the impact of a CPI compromise.� This includes classified military information or controlled unclassified information about such programs, research, technologies, processes, applications or end items.� CPI may also be unclassified information restricted by statutes (e.g., export controlled data, intellectual property, trade secrets).� (DoD Directive 5200.39, reference (a))
DL1.1.10.� Critical Research Technology (CRT).� RDT&E information identified, marked, and prioritized by site directors and managers that may be important to maintaining the U.S. warfighters� operational advantage when the resulting capability becomes part of a future DoD acquisition program or system.� CRT may be included in technology projects and may also be unclassified information restricted by statutes (e.g., export controlled data, intellectual property, trade secrets).� (DoD Directive 5200.39, reference (a))
DL1.1.11.� Defense Acquisition Deskbook.� An automated repository of information that consists of an electronic desk reference set, a tool catalog, and a forum for the exchange of information.� The reference set organizes information into two main categories:� mandatory guidance and discretionary information.� (Hereafter referred to as the �Deskbook�).
DL1.1.12.� Defense system.� A combination of elements that function together to produce the capabilities required to fulfill a DoD mission need, whether strategic or tactical, offensive or defensive, to include hardware, software, equipment, or any combination thereof.
DL1.1.13.� Delegation of Disclosure Authority Letter (DDL). A letter issued by the appropriate designated disclosure authority describing classification levels, categories, scope, and limitations related to information under a DoD Component�s disclosure jurisdiction that may be disclosed to specific foreign governments or their nationals for a specific purpose.
DL1.1.14.� Foreign Collection Threat.� The potential of a foreign interest to overtly or covertly collect information about U.S. research, technologies, acquisition program and systems, capabilities, and methods of employment that may be used to develop a similar defense system or countermeasures to the U.S. system or related operations.
DL1.1.15.� Foreign Interest.� Any foreign government, agency of a foreign government, or representative of a foreign government; any form of business enterprise or legal entity organized, chartered or incorporated under the law of any country other than the United States or its possessions and trust territories, and any person who is not a citizen or national of the United States.
DL1.1.16.� Fundamental Research.� Defined by 22 CFR Part 120.11 of the International Traffic in Arms Regulations (ITAR) (reference (e)), which implements the Arms Export Control Act (AECA) (reference (f)), as: �basic and applied research in science and engineering where the resulting information is ordinarily published and shared broadly within the scientific community, as distinguished from research the results of which are restricted for proprietary reasons or specific U.S. Government access and dissemination controls.�� 22 CFR 120.11 places fundamental research in the public domain.� However, research is not considered fundamental research if �it is funded by the U.S. Government and specific access and dissemination controls protecting information resulting from the research are applicable.�� [Note:� Executive Order 12958, (reference (g)), states in Sec 1.8 (b) that �basic scientific research information not clearly related to the national security may not be classified.�� See also NSDD 189 (reference (h)) for additional related information.]
DL1.1.17.� Horizontal Assessment and Protection.� The process that ensures research and technology associated with CPI in more than one acquisition program, or CRT associated with more than one DoD RDT&E activity, is protected to the same degree by all involved DoD Components.� (DoD Directive 5200.39, reference (a))
DL1.1.18.� Information.� Any knowledge that can be communicated or documentary material, regardless of its physical form or characteristics, that is owned by, produced by or for, or is under the control of the United States Government.� �Control� means the authority of the agency that originates information, or its successor in function, to regulate access to the information (DoD 5200.1-R, reference (c)).
DL1.1.19.� Milestone Decision Authority (MDA).� The individual designated in accordance with criteria established by the USD(AT&L), or by the ASD(C3I) for AIS acquisition programs, to approve entry of an acquisition program into the next phase of the acquisition process.� (DoD Instruction 5000.2, reference (b)).
DL1.1.20.� Militarily Critical Technologies List (MCTL).� A detailed and structured compendium of the technologies DoD assesses as critical to maintaining superior U.S. military capabilities.� It is a documented snapshot in time of the continuous MCTL process.� The DoD develops the MCTL with participation from other U. S. Government agencies, U.S. industry, and academia, and updates it on an ongoing basis.
DL1.1.21.� Multidiscipline CI (MDCI) Threat Assessment.� An assessment made by the cognizant DoD Component that describes those foreign interests that have the intent and capability to collect information about research and technology and/or a system under development.
DL1.1.22.� Operations Security (OPSEC).� A process of analyzing friendly actions attendant to military operations and other activities to do the following:
���������� DL1.1.22.1.� Identify those actions that can be observed by adversary intelligence systems.
���������� DL1.1.22.2.� Determine the indicators that hostile intelligence systems might obtain that could be interpreted or pieced together to derive critical information in time to be useful to adversaries.
���������� DL1.1.22.3.� Select and execute measures that eliminate or reduce to an acceptable level the vulnerabilities of friendly actions to adversary exploitation.�
DL1.1.23.� Program Protection Plan (PPP).� A comprehensive plan to safeguard CPI that is associated with a defense acquisition program.� The level of detail and complexity of the PPP will vary based on the criticality of the program or system, the CPI, and the phase of the acquisition process being addressed.� (DoD Directive 5200.39, reference (a)).
DL1.1.24.� Program Security Instruction (PSI).� A set of procedures to rationalize and standardize security requirements for multinational cooperative programs.
DL1.1.25.� RDT&E Site.� An installation or facility housing one or more DoD research, development, test, and evaluation (RDT&E) organizations involved with CRT and/or CPI.
DL1.1.26.� Research and Technology Protection (RTP).� The safeguarding of selected DoD research and technology anywhere in RDT&E and the acquisition process, to include the support systems for that research and technology (e.g., test and simulation equipment).� This protection activity involves integrating all security disciplines, counterintelligence, and other defensive methods to protect CRT and CPI from intelligence collection and unauthorized disclosure.
DL1.1.27.� RTP Countermeasures.� The employment of devices and/or techniques that negate an adversary�s ability to exploit vulnerabilities or impair the effectiveness of foreign interests or related activities.
DL1.1.28.� Risk Assessment.� An organized, analytical process of identifying vulnerabilities, quantifying and assessing associated risks, and implementing and/or controlling the appropriate approach for preventing or handling each risk identified.
DL1.1.29.� Security Support Plan (SSP).� A formally coordinated action plan that outlines security support for protecting CRT and CPI at specific DoD RDT&E sites and organizations that fund work efforts external to DoD, and/or within acquisition programs.
DL1.1.30.� Sensitive Information.� Any information, the loss, misuse, or unauthorized access to or modification of which could adversely affect the national interest or the conduct of Federal programs, or the privacy to which individuals are entitled under section 552a of title 5, United States Code (the Privacy Act), but which has not been specifically authorized under criteria established by an Executive order or an Act of Congress to be kept secret in the interest of national defense or foreign policy.� (Computer Security Act of 1987, reference (i)).
DL1.1.31.� Special Access Program (SAP).� A DoD program or activity (as authorized in E. O. 12958 (reference (g)), employing enhanced security measures (e.g., safeguarding, access requirements) exceeding those normally required for collateral information at the same level of classification.� (DoD 5200.1-R, reference (c)).
DL1.1.32.� System Security Engineering (SSE).� An essential element of system engineering that applies scientific and engineering principles to identify and reduce system susceptibility to damage, compromise, or destruction; the identification, evaluation, and elimination or containment of system vulnerabilities to known or postulated security threats in the operational environment.
DL1.1.33.� System Security Management Plan (SSMP).� A formal document that fully describes the planned security tasks required to meet system security engineering requirements, including organizational responsibilities, methods of accomplishment, milestones, depth of effort, and integration with other program engineering, design and management activities, and related systems.
DL1.1.34.� System Threat Assessment.� An assessment of the potential foreign threat expected to be encountered by the U.S. defense system once it is deployed in its operational environment.
DL1.1.35.� Technology.
���������� DL1.1.35.1.� The information and know-how (whether in tangible form (e.g., models, prototypes, drawings, sketches, diagrams, blueprints, manuals) or in intangible form (e.g., training or technical services)) that can be used to design, produce, manufacture, utilize, or reconstruct goods, including computer software and technical data, but not the goods themselves (50 U.S.C. 2401 et seq., reference (XX)).
���������� DL1.1.35.2.� The technical information and know-how that can be used to design, produce, manufacture, use, or reconstruct goods, including technical data and computer software.� The term does not include the goods themselves (DoD Directive 2040.2, reference (j)).
DL1.1.36.� Technology Assessment/Control Plan (TA/CP).� This document identifies and describes sensitive program information; the risks involved in foreign access to the information; the participation in the program or foreign sales of the resulting system; and the development of access controls and measures necessary to protect the U.S. technological or operational advantage of the system, as prescribed in DoD Directive 5230.11, DoD Directive 5230.20, and DoD Directive 5530.3 (references (k), (l), and (m)).
DL1.1.37.� Technology Transfer.� The intentional communication or sharing of knowledge, expertise, facilities, equipment, and other resources whether for application to military or non-military systems.� Technology transfer activities shall include, but is not limited to, the following:
���������� DL1.1.37.1.� Activities that demonstrate DoD technology; e.g., commercial, viability of technologies already developed or being developed for U.S. national security purposes.� The primary purpose of those activities, which encompass technology transfer, is to promote and make available existing DoD-owned or -developed technologies and technical infrastructure to a broad spectrum of non-DoD applications.
���������� DL1.1.37.2.� Dual-use science and technology and other related activities that develop technologies with both DoD and non-DoD applications.
���������� DL1.1.37.3.� Activities that demonstrate the U.S. national security application of technologies developed outside of the Department of Defense.� The goal is to incorporate the innovative technology into military systems to meet mission needs.
DL1.1.38.� Vulnerability. �The susceptibility of being open to exploitation, attack, or damage.
AL1.� ABBREVIATIONS AND ACRONYMS
AL1.1.� The following abbreviations and acronyms are used in this Regulation:
AL1.1.1.� ������ AECA� ��������������� Arms Export Control Act.
AL1.1.2.� ������ AIS� ������������������� Automated Information System.
AL1.1.3.�������� APB�������������������� Acquisition Program Baseline.
AL1.1.4.� ������ ASD(C3I)�� �������� Assistant Secretary of Defense for Command, Control, Communications, and Intelligence.
AL1.1.5.� ������ AT� ��������������������� Anti-Tamper.
AL1.1.6.�������� CA���������������������� Certification Authority.
AL1.1.7.�������� CAC������������������� Common Access Card.
AL1.1.8.�������� CARD����������������� Cost Analysis Requirements Document
AL1.1.9.� ������ CDRL ���������������� Contract Data Requirements List.
AL1.1.10.� ���� CFR� ������������������ Code of Federal Regulations.
AL1.1.11.� ���� CI� ���������������������� Counterintelligence.
AL1.1.12.� ���� CMI�������������������� Classified Military Information.
AL1.1.13.� ���� CIO� ������������������� Chief Information Officer.
AL1.1.14.� ���� CISP� ����������������� Counterintelligence Support Plan.
AL1.1.15.� ���� CO� �������������������� Contracting Officer.
AL1.1.16.� ���� COD������������������� Cooperative Opportunities Document.
AL1.1.17.� ���� COR� ����������������� Contracting Officer�s Representative.
AL1.1.18.� ���� CPI� ������������������� Critical Program Information.
AL1.1.19.� ���� CRD�������������������� Critical Requirements Document or Capstone Requirement Document.
AL1.1.20.������ CRT� ������������������ Critical Research Technology.
AL1.1.21.������ CUI��������������������� Controlled Unclassified Information
AL1.1.22.������ DAA������������������� Designated Approval Authority.
AL1.1.23. ����� DCID������������������ Director of Central Intelligence Directive.
AL1.1.24.� ���� DDL� ������������������ Delegation of Disclosure Authority Letter.
AL1.1.25.� ���� DFARS��������������� Defense Federal Acquisition Regulation Supplement.
AL1.1.26.� ���� DIA� ������������������� Defense Intelligence Agency.
AL1.1.27.� ���� DID� ������������������� Data Item Description.
AL1.1.28.������ DITSCAP� ��������� DoD Information Technology Security Certification and Accreditation Process.
AL1.1.29.� ���� DoD� ������������������ Department of Defense.
AL1.1.30.� ���� DOT&E� ������������ Director of Operational Test and Evaluation.
AL1.1.31.� ���� DRTPC� ������������� Defense Research and Technology Protection Council.
AL1.1.32.� ���� DSS� ������������������ Defense Security Service.
AL1.1.33.� ���� DT&E� ��������������� Developmental Test and Evaluation.
AL1.1.34.� ���� EAA� ������������������ Export Administration Act.
AL1.1.35.������ EAR�������������������� Export Administration Regulation.
AL1.1.36. ����� E.O.�������������������� Executive Order.
AL1.1.37. ����� FAR�������������������� Federal Acquisition Regulation.
AL1.1.38.� ���� FOUO� ��������������� For Official Use Only.
AL1.1.39. ����� GIG��������������������� Global Information Grid.
AL1.1.40. ����� IA������������������������ Information Assurance.
AL1.1.41.� ���� IG� ���������������������� Inspector General.
AL1.1.42.� ���� IPT� �������������������� Integrated Product Team.
AL1.1.43. ����� IT������������������������ Information Technology.
AL1.1.44.� ���� ITAR� ����������������� International Traffic in Arms Regulations.
AL1.1.45.� ���� JCAG� ���������������� Joint Counterintelligence Assessment Group.
AL1.1.46.� ���� JROC� ���������������� Joint Requirements Oversight Council.
AL1.1.47.� ���� MAIS� ���������������� Major Automated Information System.
AL1.1.48.� ���� MCTL� ��������������� Militarily Critical Technologies List.
AL1.1.49.� ���� MDA� ����������������� Milestone Decision Authority.
AL1.1.50.� ���� MDAP� �������������� Major Defense Acquisition Program.
AL1.1.51.� ���� MDCI� ��������������� Multidiscipline Counterintelligence.
AL1.1.52.� ���� MNS������������������� Mission Needs Statement.
AL1.1.53.� ���� NSDD� ��������������� National Security Decision Directive.
AL1.1.54.� ���� NSTISSP�� ��������� National Security Telecommunications and Information Systems Security Policy.
AL1.1.55.� ���� OASD(C3I)�������� Office of the Assistant Secretary of Defense for Command, Control, Communications, and Intelligence.
AL1.1.56.������ OCA������������������� Original Classification Authority
AL1.1.57.� ���� ODASD(S&IO) � Office of the Deputy Assistant Secretary of Defense for Security and Information Operations.
AL1.1.58.� ���� OIPT� ����������������� Overarching Integrated Product Team or Overarching Integrated Process Team.
AL1.1.59.� ���� OMB������������������� Office of Management and Budget.
AL1.1.60.� ���� OPSEC� ������������� Operations Security.
AL1.1.61.� ���� ORD������������������� Operational Requirements Document.
AL1.1.62.� ���� OT&E� ��������������� Operational Test and Evaluation.
AL1.1.63.� ���� OUSD(AT&L) ��� Office of the Under Secretary of Defense for Acquisition, Technology, and Logistics.
AL1.1.64.� ���� P3I� �������������������� Preplanned Product Improvement.
AL1.1.65.� ���� PEO� ������������������ Program Executive Officer.
AL1.1.66.� ���� PM� �������������������� Program Manager (also Project or Product Manager).
AL1.1.67.� ���� POC� ������������������ Point of Contact.
AL1.1.68.� ���� PPIP�������������������� Program Protection Implementation Plan.
AL1.1.69.� ���� PPP� ������������������� Program Protection Plan.
AL1.1.70.� ���� PSI� �������������������� Program Security Instruction.
AL1.1.71.� ���� R&D� ����������������� Research and Development.
AL1.1.72.� ���� RDT&E� ������������� Research, Development, Test, and Evaluation.
AL1.1.73.� ���� RFP� ������������������� Request for Proposal.
AL1.1.74.� ���� RTP� ������������������� Research and Technology Protection.
AL1.1.75.� ���� S&T� ������������������ Science and Technology.
AL1.1.76.� ���� SAE� ������������������ Service Acquisition Executives.
AL1.1.77.� ���� SAF/AQL� ��������� Director, Special Programs, Office of the Secretary of the Air Force.
AL1.1.78.� ���� SAP� ������������������ Special Access Program.
AL1.1.79.� ���� SCG�������������������� Security Classification Guide.
AL1.1.80.� ���� SEMP����������������� System Engineering Management Plan.
AL1.1.81.������ SCG�������������������� Security Classification Guide
AL1.1.82.� ���� SCOR� ��������������� Specialized C3I Operating Reference.
AL1.1.83.� ���� SOW� ����������������� Statement of Work.
AL1.1.84.� ���� SSAA������������������ System Security Authorization Agreement.
AL1.1.85.� ���� SSE� ������������������� System Security Engineering.
AL1.1.86.� ���� SSEM����������������� System Security Engineering Manager.
AL1.1.87.� ���� SSEWG�������������� System Security Engineering Working Group.
AL1.1.88.� ���� SSMP� ��������������� System Security Management Plan.
AL1.1.89.� ���� SSP� ������������������� Security Support Plan.
AL1.1.90.� ���� STA� ������������������ System Threat Assessment.
AL1.1.91.������ ST&S������������������ Director of Strategic and Tactical Systems, OUSD(AT&L).
AL1.1.92.� ���� TA/CP� ��������������� Technology Assessment / Control Plan.
AL1.1.93.� ���� U.S.C.����������������� United States Code.
AL1.1.94.� ���� USD(AT&L)� ����� Under Secretary of Defense for Acquisition, Technology, and Logistics.
AL1.1.95.� ���� USD(P)� ������������� Under Secretary of Defense for Policy.
AL1.1.96. ����� WBS������������������� Work Breakdown Structure.
AL1.1.97.� ���� WIPT� ���������������� Working-level Integrated Product Team.
PART I
GENERAL
C1. CHAPTER 1
GENERAL INFORMATION
C1.1.� PURPOSE
������� This Regulation prescribes procedures for identifying, marking, and protecting Department of Defense (DoD) research and technologies, to include critical research technology (CRT) and critical program information (CPI), in accordance with DoD Directive 5200.39, DoD Directive 5000.1, DoD Instruction 5000.2, DoD 5000.2-R, and DoD 5400.7-R (references (a), (n) (b), (o), and (p)).�
������� C1.1.1.� CRT and CPI may include classified military information and/or controlled unclassified information.�
������� C1.1.2.� Both CRT and CPI require protection to prevent unauthorized or inadvertent disclosure, destruction, transfer, alteration, or loss (hereafter referred to as �compromise�).�
������� C1.1.3.� CRT must be safeguarded in order to sustain or advance the DoD technological lead in the warfighter�s battlespace or joint operational arena.
������� C1.1.4.� The CPI, if compromised, will significantly alter program direction; unauthorized or inadvertent disclosure of the program or system capabilities; shorten the combat effective life of the system; or require additional research, development, test, and evaluation (RDT&E) resources to counter the impact of its loss.� See DL1.1.9 for CPI definition.
C1.2.� GENERAL
������� C1.2.1.� The DoD actively seeks to include foreign allies and friendly foreign countries as partners in the development, acquisition, and life-cycle management of defense systems.� Early involvement with foreign partners is encouraged by DoD, and such cooperative foreign government partnerships should begin at the requirements definition phase whenever possible.� Successful execution of cooperative programs will promote the desirable objectives of standardization, commonality, and interoperability.� The U.S. Government and its foreign government partners in these endeavors will benefit from shared development costs, reduced production, procurement costs realized from economies of scale, and strengthened domestic industrial bases.� Similarly, the DoD plays a key role in the execution of security cooperation programs that ultimately support national security objectives and foreign policy goals.� U.S. defense system sales are a major aspect of security cooperation.�
������� C1.2.2.� Increasingly, the U.S. Government relies on sophisticated technology in its defense systems for effectiveness in combat.� Technology is today�s and will be tomorrow�s force multiplier, and technology improves the warfighter�s survivability.� It is prudent and practical to protect technologies deemed so critical that their exploitation will diminish or neutralize a U.S. defense system�s effectiveness.� Protecting critical technologies preserves the U.S. Government�s resources in research and development as an investment, rather than as an expense, and enhances U.S. industrial base competitiveness in the international marketplace.�
������� C1.2.3.� Procedures and guidance in this Regulation are designed to protect CRT and CPI against compromise throughout RDT&E life cycle at all involved locations or facilities.
������� C1.2.4.� The ultimate goal is to selectively and effectively apply RTP countermeasures and counterintelligence (CI) support activities that are cost effective and consistent with risk management principles to protect CRT and CPI.
������� C1.2.5.� Anti-Tamper (AT) techniques and application of system security engineering (SSE) measures allow the United States to meet foreign customer needs for advanced systems and capabilities while ensuring the protection of U.S. technological investment and equities.� AT techniques and SSE measures are examples of protection methodologies that DoD programs use to protect critical system technologies.
������� C1.2.6.� Each DoD Component will establish RTP working groups at all RDT&E sites and appropriate headquarters to ensure comprehensive, integrated RTP programs.
C1.3.� APPLICATION
������� C1.3.1.� This Regulation applies to all the DoD Components that:
���������������� C1.3.1.1� Manage RDT&E activities,
���������������� C1.3.1.2.� Are involved in requirements generation and the acquisition of DoD systems, in accordance with DoD Directive 5000.1 (reference (n)), or
���������������� C1.3.1.3.� Are involved in providing security, intelligence, or CI support to DoD acquisition activities, DoD RDT&E activities, or DoD contractors in accordance with DoD Directive 5200.39 (reference (a)).� All intelligence and CI support must comply with DoD Directive 5240.1 and DoD Regulation 5240.1-R (references (q) and (r)).�
������� C1.3.2.� This Regulation does not apply to acquisitions by the DoD Components that involve SAPs created under the authority of E. O. 12958 (reference (g)).� The unique nature of SAPs requires compliance with special security procedures of DoD Directive O-5205.7 (reference (s)).� If the program or system contains CPI, the SAP PM will prepare and implement a PPP prior to transitioning to collateral or unclassified status.� Security, intelligence, and CI organizations should assist the SAP PM in developing the PPP.� The PPP will be provided to the offices responsible for implementing protection requirements before beginning the transition.�
������� C1.3.3.� This Regulation should be applied at all locations (to include contractor locations) where CRT and CPI are developed, produced, analyzed, maintained, employed, transported, stored, or used in training, as well as during its disposal.
C1.4.� DEFENSE RESEARCH AND TECHNOLOGY PROTECTION COUNCIL
������� C1.4.1.� The Defense Research and Technology Protection Council (DRTPC) will provide oversight for continued protection of CRT and CPI within DoD from research through acquisition and operation to disposal.�
������� C1.4.2.� The DRTPC will be chaired by an Under Secretary of Defense for Acquisition, Technology, and Logistics (USD(AT&L)) representative and consist of representatives from Under Secretary of Defense for Policy (USD(P)), Director of Defense Research and Engineering (DDR&E), ASD(C3I), Director of Operational Test and Evaluation (DOT&E), and appropriate DoD Components.
������� C1.4.3.� The DRTPC will have the following responsibilities.
�������������� C1.4.3.1.� Ensure that DoD-funded critical research, technologies, and development activities are appropriately protected as outlined in DoD Directive 5200.39 (reference (a)) and this regulation.
�������������� C1.4.3.2.� Approve DoD RTP training within all DoD Components.�
�������������� C1.4.3.3.� Ensure that Defense Service Management College and DoD Components consistently incorporate mandatory training on DoD RTP in updated course curriculum.
�������������� C1.4.3.4.� Provide recommendations on RTP policy,
procedures, and processes, as appropriate.
�������������� C1.4.3.5.� When the same CRT or CPI exists under two or more managers, in two or more acquisition programs, or is associated with two or more DoD RDT&E activities, and the managers cannot reach agreement on a consistent protection measure, the issue will be raised to the DRTPC for adjudication.� This will ensure that all involved DoD Components protect similar CRT or CPI to the same degree.
C1.5.� RTP PROTECTION PLANNING
������� C1.5.1.� Protection planning begins with the identification of dual use and military application of research and technology and extends through to demilitarization.� Therefore, CRT and CPI will be protected from their point of identification through their life cycle to property disposal.
������� C1.5.2.� Research technology will be continuously reviewed and CRT identified within each of the seven subcategories of RDT&E. A Security Classification Guide (SCG) will be developed for all classified CRT and related information requiring controls as specified in the references in enclosure 3.� Initial foreign disclosure guidance will be prepared, when appropriate.� This information shall be updated when CRT moves between the subcategories of Science and Technology.� CRT shall be updated, validated, and forwarded to the PM when incorporated into an acquisition.
������� C1.5.3.� Identification of CPI shall begin with preparation of the Mission Needs Statement (MNS).� A SCG will be developed for all classified CPI and related information requiring controls as specified in the references in enclosure 3.� Initial foreign disclosure guidance will be prepared, when appropriate.� This information shall be updated for the initial and subsequent Capstone Requirement Document (CRD) (if required) and the Operational Requirements Document (ORD).� CPI shall be updated, validated, and forwarded for evaluation or comment prior to approval at each milestone review.
������� C1.5.4.� Protection of CRT and CPI will range from providing threat awareness education to scientists and engineers performing fundamental research, to the implementation of a program protection plan (PPP).
������� C1.5.5.� While CRT and/or CPI may be individually unclassified, the compilation and aggregation of CRT and CPI within information technology (IT) systems or databases may reveal classified information.� SCGs must address this possibility.� RDT&E Site Directors and PMs shall review all databases and IT systems processing, storing, communicating, or analyzing multiple CRT and/or CPI, which are individually unclassified, for compilation of information becoming classified as stated in their SCG.� In those cases where the compilation of information reveals classified information, that IT system or database shall be appropriately marked, operated and protected as classified information in accordance with DoD 5200.1-R (reference (c)) or DoD 5220.22-M (reference (t)), as appropriate.� When the review reveals no existing security classification guidance on the compilation of CRT and/or CPI that should be classified, the cognizant Original Classification Authority (OCA) shall be notified immediately for a formal security classification determination.� The IT system or database will be protected as classified information until the OCA completes the formal security classification determination.� All web sites containing CRT and CPI are included within the compilation review requirement.
C1.6.� MARKING, DISSEMINATION AND DESTRUCTION OF CRT AND CPI.
������� C1.6.1.� General Provisions for Marking of CRT and CPI.
���������������� C1.6.1.1.� All CRT and CPI will be clearly identified by electronic labeling, marking, or similar designation.� If physically marking the medium containing CRT or CPI is not possible, identification of CRT and CPI will be accomplished by other means.� CRT and CPI markings must be conspicuous.� The term "marking" includes other concepts of identification and is the principal means of informing holders of CRT or CPI about specific protection requirements for that information.� Marking or otherwise designating CRT or CPI is the specific responsibility of the original determining or derivative authorities.� CRT and/or CPI markings will be in addition to any classification markings in accordance with DoD 5200.1-R (reference (c)).� Marking and designations serve these purposes:
���������������� C1.6.1.2.� Alert holders to the presence of CRT and CPI.
���������������� C1.6.1.3.� Identify the exact information needing protection as specifically as practicable.
���������������� C1.6.1.4.� Warn holders of special control or safeguarding requirements.
������� C1.6.2.� Exceptions.� No information that is within the public domain, as defined by the ITAR (reference (e)), shall be marked as CRT or CPI.� The appearance of CRT or CPI in a newspaper, magazine, or other public media is not justification for the removal of CRT or CPI markings.
������� C1.6.3.� Marking CRT or CPI documents and other material.� Material other than ordinary paper documents must have the same information either marked on it or appears on all printed copies of the CRT and CPI.� CRT and CPI documents must bear the following markings:
���������������� C1.6.3.1.� Any classification markings as required by DoD 5200.1-R (reference (c)).
���������������� C1.6.3.2.� The agency, office of origin, and date of the determination.
���������������� C1.6.3.3.� Control notice or other marking that may apply to the CRT or CPI.
���������������� C1.6.3.4.� Holders of improperly marked CRT or CPI should contact the document originator to obtain the correct determination and appropriate marking.
������� C1.6.4.� Overall CRT and/or CPI Markings.� Each CRT or CPI document must be clearly marked and conspicuous to alert persons handling the document that it contains CRT or CPI.� The CRT and/or CPI designation will be marked, stamped, or affixed (with a sticker, tape, etc.) on the front cover or first page at the bottom and the outside of the back cover or last page.
������� C1.6.5.� Removal Instructions.� Information designated as CRT or CPI will be protected until the original authority determines protection is no longer required.� The marking shall be removed from the document and annotated by the original determination authority with the date of the determination.� The original authority may issue a letter of determination to remove science, research, and technologies information from the CRT or CPI designation.
������� C1.6.6.� CRT Markings.�
���������������� C1.6.6.1. �Each page of a document containing CRT shall be conspicuously marked at the bottom.� These markings must stand out from the balance of the information and thus a particular size is not specified.� Pages containing only CRT shall be marked, �CRITICAL RESEARCH TECHNOLOGY.�� Blank interior pages will not be marked.
���������������� C1.6.6.2.� Parenthetical portion markings will be (CRT).� The marking �CRT� will be used in conjunction with other classification marking as specified in DoD 5200.1-R (reference (c)).
���������������� C1.6.6.3.� Unless another Directive or statute prescribes different additional markings, these control notices shall be placed on the face of the document.
CRITICAL RESEARCH TECHNOLOGY
This material contains critical research technology as defined by DoDD 5200.39.� Unauthorized disclosure subject to administrative and/or criminal sanctions.� Requires specific formal authorization for foreign dissemination.
������� C1.6.7.� CPI Markings.�
���������������� C1.6.7.1.� Each page of a document containing CPI shall be conspicuously marked at the bottom.� These markings must stand out from the balance of the information and thus a particular size is not specified.� Pages containing only CPI shall be marked, �CRITICAL PROGRAM INFORMATION.�� Blank interior pages will not be marked.
���������������� C1.6.7.2.� Parenthetical portion markings will be (CPI).� The marking "CPI" will be used in conjunction with other classification marking as specified in DoD 5200.1-R (reference (c)).
���������������� C1.6.7.3.� Unless another Directive or statute prescribes different additional markings, these control notices shall be placed on the face of the document.
CRITICAL PROGRAM INFORMATION
This material contains critical research technology as defined by DoDD 5200.39.� Unauthorized disclosure subject to administrative and/or criminal sanctions.� Requires specific formal authorization for foreign dissemination.
5 U.S.C. 552 (b)(3), (b)(4), or (b)(5) exemption applies.
������� C1.6.8.� Military Components may develop CRT or CPI document cover sheets.
������� C1.6.9.� CRT or CPI documents and information may be stored in lockable containers unless it is classified information, which will be in accordance with DoD 5200.1-R (reference (c)).� CRT and/or CPI documents are not authorized for public disclosure nor disclosure to any foreign entity without formal review by the original determination or higher authority.
������� C1.6.10.� DoD 5200.1-R (reference (c)) shall be revised to include these provisions upon next revision.
������� C1.6.11.� Disposition and Destruction of CRT and CPI.
���������������� C1.6.11.1.� CRT or CPI documents and other material will be retained within DoD organizations and RDT&E sites only if they are required for effective and efficient operation of the organization or if law or regulation requires their retention.� Documents that are no longer required for operational purposes shall be disposed of in accordance with the provisions of the Federal Records Action (Chapters 21, 31, and 33 of 44 U.S.C.) (references (u), (v), and (w)) and appropriate implementing directives and records schedules.�
���������������� C1.6.11.2.� Material that has been identified for destruction shall continue to be protected, as appropriate, until it is actually destroyed.
���������������� C1.6.11.3.� Destruction of CRT or CPI documents and material will be accomplished by means that eliminate risk of reconstruction of the CRT and CPI.� CRT or CPI identified for destruction shall be destroyed completely to preclude recognition or reconstruction of the CRT or CPI in accordance with procedures and methods prescribed by the Head of the DoD Component or their designee.� At a minimum, for unclassified information, CRT and/or CPI will be destroyed using the same standards as For Official Use Only.
C1.7.� OVERVIEW - PROTECTION OF CRT AT RDT&E ACTIVITIES
������� C1.7.1.� Protection can apply to all seven subcategories of RDT&E (see DoD 7000.14-R, Volume IIB (reference (x))).� DoD Directive 5200.39 (reference (a)) recognizes the normally unrestricted nature of fundamental research, as identified in National Security Decision Directive (NSDD) 189 (reference (h)), and as further stipulated for Basic Research in Executive Order 12958 (reference (g)).� The term �fundamental research� refers generally to Basic Research (6.1) and Applied Research (6.2), and is defined in the International Traffic in Arms Regulations (ITAR) (reference (e)).
������� C1.7.2.� A site-specific CI Support Plan (CISP) and a site-specific Security Support Plan (SSP) shall be prepared for each RDT&E site.
������� C1.7.3.� RDT&E commanding officers, site directors, or their designees (hereafter referred to as �site directors�) shall identify and prioritize their CRT, and communicate the results to CI, security, foreign disclosure, operations security (OPSEC), and intelligence organizations.
������� C1.7.4.� Intelligence organizations shall provide information on technical capabilities of adversaries in specific RDT&E programs or projects.
������� C1.7.5.� Working together, RDT&E, CI, security, foreign disclosure, OPSEC, and intelligence organizations shall use an interactive process to safeguard CRT from compromise in order to sustain or advance the DoD technological lead in the future battlespace.
������� C1.7.6.� Site directors, in coordination with security, intelligence, and CI specialists, will ensure that assigned personnel receive tailored threat briefings.
C1.8.� OVERVIEW - PROTECTION OF CPI IN
ACQUISITION
������� C1.8.1.� Program protection planning must begin with requirements generation as described in Chairman of the Joint Chiefs of Staff Instruction 3170.01B (reference (y)).� It is an integral part of the overall acquisition strategy, which is typically developed prior to formal designation of an acquisition program.� Any acquisition effort must, at a minimum, be evaluated in terms of the need to protect its CPI.� The resources (e.g., personnel, fiscal, AISs) needed to accomplish that evaluation must be identified as early as possible, but not later than entry into Milestone B.�
������� C1.8.2.� Each program will be reviewed by the PM (or the responsible commander/manager if a PM has not been appointed) to determine if the program contains CPI.� This examination will also consider CRT previously identified by DoD laboratories, as well as CPI inherited from another program, or as a result of non-traditional acquisition techniques (e.g., Advanced Concept Technology Demonstration, flexible technology insertion).
������� C1.8.3.� The PM (or the responsible commander/manager if a PM has not been appointed), with the assistance of a working-level IPT (WIPT), makes the determination as to the existence of CPI that need protection.� The need for research and technology protection is based on identifying critical technologies, systems, and/or information that are designated as the program�s CPI.
���������������� C1.8.3.1.� If it is determined there is no CPI associated with the program (neither integral to the program nor inherited from a supporting program), a program protection plan (PPP) is not required.� The PM shall make this determination in writing.� The Program Executive Officer, Service Acquisition Executive, or MDA will approve this determination.
���������������� C1.8.3.2.� If a program contains CPI, program protection planning (see C6. Chapter 6) will be followed.� The PM (or other official as noted above), with the assistance of a WIPT and appropriate support activities, is responsible for developing and implementing a PPP.� The PPP will be developed, as required, beginning in the Component Advanced Development, Pre-Systems Acquisition phase and be available to the MDA at Milestone B and at all subsequent milestones during the life cycle of the program.� The PPP will be revised and updated once every three years or as required by changes to acquisition program status or the projected threat.
������� C1.8.4.� When a program contains CPI, a multidisciplinary CI threat assessment (by Service CI organization), CPI vulnerability assessment (by supporting security organization), and technology risk assessment (by supporting intelligence organization) shall be prepared to determine the threat against the CPI.� At the time of the initial evaluation to determine the program�s CPI, a determination of whether there will be foreign involvement or access to the program, system, or system information, should be made by a Joint Mission Analysis Work Group organized pursuant to Chairman of the Joint Chiefs of Staff Instruction 3170.01B (reference (y)).� These assessments shall provide the basis for risk management decisions and for identification of appropriate cost-effective RTP countermeasures required to negate or minimize the threat.
������� C1.8.5.� At any time in the requirements generation or acquisition process, when it is determined that foreign participation in system development is possible or an allied system will be used, the system to be developed is a candidate for foreign sales or direct commercial sale, the system will be used in multinational operations or other cooperative programs, a Technology Assessment/Control Plan (TA/CP) and Delegation of Disclosure Authority Letter (DDL) shall be prepared as annexes to the PPP.� If foreign involvement is initiated prior to the appointment of a PM, the DoD Component that generates the system requirement shall initially prepare this documentation for validation by the Joint Requirements Oversight Council (JROC) and approval by the MDA.� These requirements and the preparation of the PPP, TA/CP, DDL, and supporting documentation shall be assumed by the PM, at the time of the appointment of the PM.
������� C1.8.6.� Regardless of the extent of protection efforts required to support an acquisition program, personnel and fiscal resource requirements should be identified early in acquisition program developments as an integral part of the overall acquisition strategy and planning.
C1.9.� OVERVIEW � SECURITY SUPPORT PLAN (SSP)
������� C1.9.1.� The SSP will identify the tailored security support for the site directors who have CRT or CPI provided by PMs.�
������� C1.9.2.� Each site, base, or installation that hosts CRT and CPI will have a SSP.�
������� C1.9.3.� The SSP will be reviewed annually and updated as necessary.
C1.10.� OVERVIEW - COUNTERINTELLIGENCE SUPPORT PLAN (CISP)
������� C1.10.1.� The CISP will identify the tailored CI support for RDT&E facilities with CRT and PMs of acquisition programs with CPI.�
������� C1.10.2.� Each individual RDT&E site with CRT and each acquisition program with CPI will have a CISP.�
������� C1.10.3.� The CISP will be signed by the customer organization and the servicing CI organization.� The CISP will specify which of the CI activities will be conducted in support of the facility or program, and will provide the CI personnel with information about the program or facility to help focus the CI activities.
������� C1.10.4.� The CISP will be reviewed annually, or as required by events, and used as the baseline for any evaluation of the program or facility and its supporting CI program.
C1.11.� ANTI-TAMPER
���������� C1.11.1.� Anti-Tamper (AT) measures are to be developed and implemented by acquisition PMs to protect CRT and/or CPI in U.S. systems that may be developed with or sold to foreign governments, or that may no longer be within U.S. control (e.g., theft, battlefield loss).� AT guidelines apply to system performance, materials, hardware, software, algorithms, design and production methods, maintenance and logistical support, and other facets as determined by competent acquisition authority.� Although protective in nature, AT is not a substitute for appropriate program protection or other security measures.
���������� C1.11.2.� Properly employed, AT will add longevity to a critical technology by deterring efforts to reverse-engineer, exploit, or develop countermeasures against a system or system component.� AT is not intended to completely defeat such hostile attempts, but it should discourage exploitation or reverse-engineering, or make such efforts so time-consuming, difficult, and expensive that even if successful, a critical technology will have been replaced by its next-generation version.�
���������� C1.11.3.� AT is intended to buy time for the U.S. and its allies to further develop critical technologies so that successful exploitation of earlier generations does not constitute a threat to their military forces and capabilities.
C1.12.� DEFENSE ACQUISITION DESKBOOK
Guidance on the application of program protection is included the Defense Acquisition Deskbook (DAD).� The DAD is an automated reference tool that provides acquisition information for all the DoD Components across all functional disciplines.� The DAD will contain DoD Directive 5200.39 (reference (a)) and this Regulation.� The DoD Components may also include their local implementing guidance, with examples, in their section of the DAD.�
C1.13.� SPECIALIZED C3I OPERATING REFERENCE (SCOR)
SCOR is an automated reference tool similar to the DAD that provides information on security and CI areas for all the DoD Components across all related disciplines.� Additional guidance for RTP and background information on protective measures is contained in the SCOR.
C1.14.� ECONOMIC ESPIONAGE
������� C1.14.1.� The Economic Espionage Act of 1996, Section 1831 et seq. of 18 U.S.C. (reference (z)) highlighted the concerns of the U.S. Government and U.S. industry on foreign economic collection and economic espionage.� In an effort to reduce the loss of industrial, technical, financial, and proprietary commercial and U.S. Government information, reference (z) makes the theft or misappropriation of trade secrets a Federal criminal offense.� Trade secrets include business, scientific, technical, engineering, and economic information (e.g., patterns, compilations, programs, methods, processes, and codes whether tangible or intangible).�
������� C1.14.2.� Reference (z) imposes up to a 15-year prison
term and/or $500,000 fine for any person, or $10 million fine on any
organization that steals or destroys a trade secret with the intent to benefit
a foreign power.� Penalties may also be
imposed on an individual or corporation if the theft of the information is
intended to economically benefit anyone other than the owner of the trade
secret, or injure the owner of the trade secret.� Reference (z) also requires courts to endeavor to minimize
further disclosure of the trade secret during the pendency of the prosecution
in order to encourage victims to report theft.
������� C1.14.3.� The theft or misappropriation of U.S. proprietary information or trade secrets, especially to foreign governments and their agents, directly threatens the economic competitiveness of the U.S. economy.� Increasingly, foreign governments through a variety of means, actively target U.S. businesses, academic centers, and scientific development to obtain critical technologies and thereby provide their own economies with an advantage.� Industrial espionage, by both traditionally friendly nations and recognized adversaries, proliferated throughout the 1990s.
C1.15.� INFORMATION REPORTING REQUIREMENTS
Incidents
of loss, compromise, or theft of proprietary information or trade secrets
involving CRT and CPI, shall be immediately reported, in accordance with DoD
Instruction 5240.4, DoD Directive 5200.1, and Section 1831 et seq.
of 18 U.S.C. (references (aa), (bb), and (z)).�
Such incidents shall be immediately reported to the Defense Security
Service (DSS), the Federal Bureau of Investigation, or the applicable DoD
Component CI and law enforcement organizations.� If the theft of trade secrets or proprietary information might
reasonably be expected to affect DoD contracting, DSS should notify the local
office of the Federal Bureau of Investigation.
C1.16.� TECHNOLOGY PROTECTION RESOURCE DIRECTORY
Individuals who prepare requirements documents, the JROC, IPTs, PMs, site directors, and supporting security, foreign disclosure, intelligence, and CI activities should refer to the Specialized C3I Operating Reference to identify subject matter experts from whom assistance may be obtained.
C1.17.� REGULATION OVERVIEW
This Regulation is divided into four parts as follows.
������� C1.17.1.� Part I includes general information on the purpose and scope of DoD�s RTP effort.
������� C1.17.2.� Part II contains the procedures for RTP at RDT&E facilities.
������� C1.17.3.� Part III contains the procedures that are to be followed to protect acquisition program technologies and information.
������� C1.17.4.� Part IV discusses the procedures in security, CI, anti-tamper, horizontal assessment and protection, RTP assessment and inspection, and information assurance that apply to RTP activities, both at RDT&E sites and within acquisition programs.
PART II
PROTECTION OF RESEARCH AND TECHNOLOGY
AT RDT&E ACTIVITIES
C2.� CHAPTER 2
RDT&E ACTIVITY PROTECTION STRATEGY
C2.1.�
GENERAL
The purpose of RDT&E activity protection is to safeguard DoD RDT&E information from unauthorized disclosure to foreign interests.� CI and security specialists will provide a wide range of services to ensure personnel assigned to the RDT&E sites are aware of the threat from foreign intelligence services, other foreign interests, or anyone involved in the unauthorized acquisition of DoD information.
C2.2�
PROTECTION APPROACHES
���������� C2.2.1.� RDT&E conducted within the DoD and by DoD contractors is covered by the following policies:
�������������� C2.2.1.1.� Disclosure of both classified military information and unclassified technical data� (DoD Directive 5230.11, �Disclosure of Classified Military Information (CMI) to Foreign Governments and International Organizations,� (reference (k)); DoD Directive 5230.24, �Distribution Statements on Technical Documents,� (reference (cc));� DoD Directive 5230.25, �Withholding of Unclassified Technical Data from Public Disclosure� (reference (dd)), International Traffic in Arms Regulation (reference (e)), and Export Administration Regulations, (reference (ee)).�
�������������� C2.2.1.2.� Control of foreign visitors� (DoD Directive 5230.20, �Visits, Assignments, and Exchanges of Foreign Nationals,� (reference (l)).
�������������� C2.2.1.3.� Export control� (DoD Directive 2040.2, �International Transfers of Technology, Goods, Services, and Munitions,� (reference (j)).
���������� C2.2.2.� Making these policies effective within the RDT&E environment requires training and awareness of the policies, and the required procedures to be followed, as well as an integration of these efforts to ensure the identification of CRT, the identification of the applicable safeguard, and the effective application of that safeguard.
���������� C2.2.3.� To aid in the formulation of an effective protection program at each RDT&E site, a SSP and a CISP will be prepared (see C12 and C13. Chapters 12 and 13).� These documents will be developed by the RDT&E site directors in concert with the support organizations (CI, security, foreign disclosure, OPSEC, and intelligence).
C3.� CHAPTER 3
PROTECTION PLANNING FOR RDT&E ACTIVITIES
C3.1.� GENERAL
Effective RTP planning depends on a process of identifying CRT and applying the appropriate awareness and safeguarding actions.� The process consists of:
������� C3.1.1.� Identifying, and prioritizing, whenever possible, the CRT.
������� C3.1.2.� Conducting an awareness program to ensure that RDT&E site personnel understand the threat to U.S. research and technologies and the existing programs to counter the identified threat.
������� C3.1.3.� Selecting appropriate countermeasures to protect the CRT.
������� C3.1.4.� Identifying CI support to be provided at each RDT&E site.
������� C3.1.5.� Preparing a SSP that will consolidate security actions at the RDT&E site.
������� C3.1.6.� Preparing a CISP that will serve as the �contract� between the individual RDT&E site director and the responsible CI support activity.
C3.2.� IDENTIFICATION OF CRITICAL RESEARCH� TECHNOLOGY (CRT)
������� C3.2.1.� RDT&E site directors shall identify and prioritize their CRT, and communicate them to CI, security, foreign disclosure, OPSEC, and intelligence organizations, as appropriate.
������� C3.2.2.� The CRT will be identified in the applicable CISP.
C3.3.� PROTECTION TRAINING AND AWARENESS
������� C3.3.1.� Training is an essential part of the
protection strategy for RDT&E activities.�
Personnel engaged in all categories of DoD RDT&E, including those
involved solely in fundamental (Basic and Applied) research, should receive
tailored threat awareness briefings.�
������� C3.3.2.� RDT&E, intelligence, CI, and security
personnel must be knowledgeable of DoD directives that govern disclosure of
both classified military information and unclassified technical data to foreign
entities and into the public domain.�
These include DoD Directives 5230.11 (reference (k)), DoD Directive 5230.20
(reference (l)), DoD Directive 5230.24 (reference (cc)), and DoD Directive
5230.25 (reference (dd)).
������� C3.3.3.� RDT&E, intelligence, CI, and security
personnel should also be familiar with the Export Administration Regulation
(EAR), 15 Code of Federal Regulations (CFR), part 730, implementing the Export
Administration Act (EAA) (reference (ee)) which pertains to dual-use
commodities; the International Traffic in Arms Regulation (ITAR), 22 CFR 120,
(reference (e)) which implements the Arms Export Control Act (AECA), which
controls the export of defense articles and services; and DoD Directive 2040.2,
�International Transfers of Technology, Goods, Services, and Munitions,�
(reference (j)) which implements relevant portions of the EAA and the
AECA.�
������� C3.3.4.� RDT&E, intelligence, CI, and security
personnel must understand restrictions on the export of munitions list items as
specified in the ITAR (reference (e)) and commodities list items as outlined in
the EAR (reference (ee)).�
������� C3.3.5.� It is imperative that RDT&E,
intelligence, CI, and security personnel understand that dissemination of
technical data related to munitions or commodities list items constitutes an
export.� They must know when the oral,
visual, or written disclosure of technical data to a foreign national may
require a �deemed� export license.�
Ensuring that RDT&E personnel understand and follow the guidance
contained in the directives and regulations cited in paragraphs C3.3.2 through
C3.3.4, will contribute significantly to the protection of research and
technology in RDT&E facilities.
C3.4.� APPLICATION OF SAFEGUARDS
������� C3.4.1.� Site directors are responsible for determining the applicability of safeguards to all elements of the site�s RDT&E program.� Site directors, or their designees, will:
���������� C3.4.1.1.� Review the site RDT&E program periodically and/or whenever there is a significant change.
���������� C3.4.1.2.� Identify RDT&E information within the program that has already been identified for safeguarding (e.g., export control, distribution statements, special handling caveats).
���������� C3.4.1.3.� Identify additional RDT&E information that deserves increased RTP awareness and/or training based on the potential military application, significance of the technological advances, or other factors.
���������� C3.4.1.4.� Prepare, with supporting organizations (CI, security, foreign disclosure, OPSEC, and intelligence), a CISP and a SSP that are tailored to focus the limited protection resources on the identified CRT.
���������� C3.4.1.5.� Ensure RDT&E information identified as CRT is appropriately marked and disseminated (e.g. export control, distribution statements, special handling caveats).
������� C3.4.2.�
Unclassified Technical Data .�
The site director will:
���������� C3.4.2.1.� Establish a process whereby RDT&E personnel determine dissemination restrictions on technical data generated in the facility.� This process will apply to new RDT&E work, work in progress, completed work, and to reports and documentation resulting from completed work.
���������� C3.4.2.2.� Ensure that personnel understand the requirements to obtain approval for all public releases.
���������� C3.4.2.3.� Provide training for RDT&E personnel on DoD Directive 5230.24 (reference (cc)) and DoD Directive 5230.25 (reference (dd)).
���������� C3.4.2.4.� Ensure personnel understand the security requirements for transmitting Controlled Unclassified Information (CUI), CRT, and CPI via telephone, facsimile, and/or e-mail systems.
������� C3.4.3.� Assignments, Visits, and Exchanges of Foreign Representatives.� The site director will:
���������� C3.4.3.1.� Establish a process for approving visits by foreign nationals that will include dissemination of appropriate disclosure rules and restrictions to RDT&E personnel being visited.
���������� C3.4.3.2.� Establish a process for archiving information about foreign national visits including but not limited to, information about the visitor, reason for visit, information disclosed, and any anomaly that occurs during the visit.
���������� C3.4.3.3.� Ensure that foreign visitors are visually identifiable as required by DoD Directive 5230.20 (reference (l)).� Foreign nationals will be issued and wear facility access control or physical security badges when in DoD RDT&E facilities.� When DoD Identification Cards or DoD Common Access Card (CAC) for foreign nationals are employed, ensure that foreign nationals are properly trained on their usage while at DoD RDT&E sites.
���������� C3.4.3.4.� Mandate training in the handling of foreign visitors, representatives and exchange officers (DoD Directive 5230.20 (reference (l))).� Ensure that a contact officer has been appointed for each foreign national and they are informed of the disclosures authorized for each visitor by category of information/data.
���������� C3.4.3.5. Ensure that foreign nationals are appropriately connected to and identified on IT networks and systems, to include e-mail systems, in accordance DoD Directive 5230.20 (reference (l)).
���������� C3.4.3.6. Ensure that foreign nationals identify themselves as foreign nationals when using the telephone and conducting business with DoD and other Federal agencies (DoD Directive 5230.20 (reference (l))).
���������� C3.4.3.7. Ensure that CRT releases under the provision of a Data Exchange Agreements or Master Exchange Agreements are reviewed and approved prior to release.
������� C3.4.4.�
Export Control.� The site
director will:
���������� C3.4.4.1.� Establish a process whereby RDT&E personnel determine whether technical data or commodities at RDT&E facilities can be exported to foreign countries.
���������� C3.4.4.2.� Establish a focal point at each RDT&E site to determine whether a deemed export license is required when a foreign national visits the facility.
���������� C3.4.4.3.� Mandate training requirements for personnel at DoD research facilities on the deemed export licensing requirements of the EAR (reference (ee)) and the ITAR (reference (e)) and on other mechanisms, such as international agreements, whereby data may be legally exported.
���������� C3.4.4.4.� Ensure personnel understand the security requirements for transmitting export controlled technical data, CRT, and CPI via telephone, facsimile, and/or e-mail systems.
C3.5.� SECURITY SUPPORT PLAN
Analogous to a PPP for acquisition programs, an SSP will be developed for each RDT&E site as described in C13.� Chapter 13.� This plan will serve as the consolidated plan for integrating all security, foreign disclosure, intelligence, CI, and OPSEC activities at the site.
C3.6.� COUNTERINTELLIGENCE (CI) SUPPORT PLAN (CISP)
The CI support for each RDT&E site will be tailored as described in C4.� Chapter 4.� A CISP will be developed for each RDT&E site as described in C14.� Chapter 14.� This plan will serve as the �contract� between the individual RDT&E site director and the responsible CI support activity.
C3.7.� INFORMATION ASSURANCE
All IT network and systems storing,
processing, or transmitting CRT will be accredited in accordance with Defense
Information Technology Systems Certification and Accreditation Program as
described in C18.� Chapter 18.
C4.� CHAPTER 4
COUNTERINTELLIGENCE
SUPPORT TO RDT&E ACTIVITIES
C4.1.� CI SUPPORT AT DoD RDT&E ACTIVITIES
������� C4.1.1.� DoD Component CI agencies will assign CI
specialists to support DoD RDT&E activities on or off military
installations.
������� C4.1.2.� These CI specialists will:
�������������� C4.1.2.1.� Provide full-time, tailored, protection
support to major DoD RDT&E sites and �on-call� support to any DoD RDT&E
sites not requiring the full-time presence of CI specialists.
�������������� C4.1.2.2.� Provide CI support to DoD contractors and academic institutions working with DoD CRT in coordination with the Defense Security Service (DSS).
�������� C4.1.3.� DoD Component CI agencies
will:
�������������� C4.1.3.1.� Assign a CI specialist to the DoD Component
headquarters or major command acquisition and technology element to provide CI
support to DoD Component research projects and acquisition programs.
�������������� C4.1.3.2.� Ensure all field CI personnel involved in
RTP receive specialized CI training from the Joint CI Training Academy.
�������������� C4.1.3.3.� Ensure that appropriate security, research
management, foreign disclosure, OPSEC, and acquisition program personnel are
continuously apprised of foreign intelligence or other threat information
relating to their RDT&E site or research projects.
�������������� C4.1.3.4.� Disseminate CI information and products to
contractor facilities under DSS cognizance and to locations and officials DSS
may designate.
�������������� C4.1.3.5.� Keep DSS informed of any threat to CRT
and/or CPI that involve contractors under the cognizance of DSS.� The provision of classified threat
information to contractors shall be coordinated with DSS.
�������������� C4.1.3.6.� Provide
requested threat information to assist defense contractors in developing and
updating their Technology Control Plans and protection of DoD CRT.
���������� C4.1.4.� The DoD Joint CI Assessment Group (JCAG) provides a centralized CI assessment capability supporting horizontal assessment and protection, threat analysis, and other RTP activities.
PART III
PROTECTION OF CPI IN ACQUISITION PROGRAMS
C5. CHAPTER 5
PROGRAM PROTECTION STRATEGY
C5.1.� GENERAL
������� C5.1.1.� The initial steps for planning program protection must be taken early in the acquisition cycle to ensure protection of CPI.� This effort will be a major factor in avoiding additional and unforeseen program costs.� Protection planning begins before a program or system is designated as an acquisition program.� Early planning will ensure that necessary personnel and fiscal resource requirements are identified for applicable funding consideration.
������� C5.1.2.� Program protection planning may be outsourced and included in a contract.� That contract activity may include initial program and system evaluation as well as program protection planning that leads to specific RTP countermeasures.� Early planning is necessary to ensure that funds are programmed and budgeted to provide the required contract support.
������� C5.1.3.� Program protection activities must begin prior to contract award.� Delaying the process may result in safeguards being difficult to accomplish or being omitted from contracts.� The program�s underpinning CRT and inherited or determined CPI must be factored into the program�s overall acquisition strategy.� PMs who are responsible for this planning must budget for all security costs within the Planning, Programming, and Budget System and the program�s Acquisition Program Baseline.
C5.2.� PROGRAM PROTECTION STRATEGY.�
������� C5.2.1.� Each agency must apply procedures early in its acquisition cycle to ensure program protection requirements are properly addressed (see figure C5.F1.).� The generic procedures must be tailored for the specific acquisition program or system being addressed.
���������������� C5.2.1.1.� Acquisition planning must consider program protection an integral part of the acquisition strategy early in the planning cycle.� This includes ensuring that the program management staff (whether or not a PM has been officially designated) has a representative who does the following:
���������������������������� C5.2.1.1.1.� Understands program protection planning.
���������������������������� C5.2.1.1.2.� Is able to identify requirements that must be programmed and budgeted.
���������������������������� C5.2.1.1.3.� Is tasked with including program protection expertise on the program management staff.�
������� C5.2.2.� The first step is to identify resources and assign program protection staff.� This should be accomplished during the early requirements reviews, but not later than the beginning of the Components Advanced Development phase.� When program protection is outsourced, program protection requirements must be included in appropriate portions of solicitations and resulting contracts (e.g., statement of work (SOW), Contract Data Requirements List (CDRL), DD Form 254).
������� C5.2.3.� The next step is to assist the program management staff in translating protection requirements into a program protection plan (PPP).� This should be accomplished during a working-level IPT (WIPT) process.� Acquisition strategy reviews may require an acquisition plan, depending on the size and complexity of the acquisition.� This plan should detail the program protection requirements, funding, and methodology to meet these requirements.
������� C5.2.4.� The final step is strategy implementation. �This will result in an event-based schedule to execute the acquisition strategy and include actions that address program protection.� After this foundation is laid, the program will proceed through the milestones and phases shown in Figure C5.F1.� The program protection activities, described in C6.� Chapter 6 through C11.� Chapter 11, are tailored and performed prior to each milestone to provide the required countermeasures during each acquisition phase.�
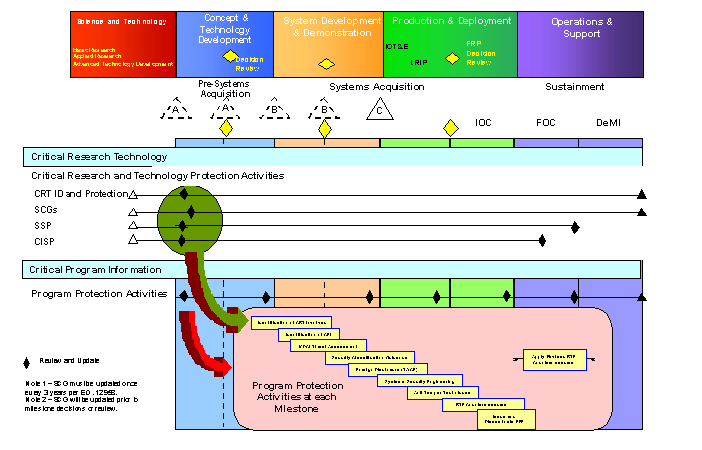
Figure C5.F1.� Acquisition Program Schedule
C6. CHAPTER 6
PROGRAM PROTECTION PLANNING
C6.1.� GENERAL
������� C6.1.1.� Effective program protection planning is the process of identifying CPI and determining necessary countermeasures to safeguard the CPI throughout the acquisition process.� CPI includes defense technologies and their support systems as defined in DoD Directive 5200.39 (reference (a)).� To accomplish program protection objectives, each DoD acquisition program will be reviewed by the PM (or the responsible commander/manager if a PM has not been appointed) to determine if the program contains CPI.� Not all acquisition programs will contain CPI.� When the PM decides that there is no CPI, this determination shall be put in writing for concurrence by the appropriate level Program Executive Officer, Service Acquisition Executive, or MDA.� If the acquisition program does contain CPI, the program protection planning process should address the following:
���������������� C6.1.1.1.� Identify and set priorities on those operational or design characteristics of the system that result in the system providing unique mission capabilities.
���������������� C6.1.1.2.� Identify and prioritize, in terms of importance to the program or to the system being developed, CPI related to these distinctive system characteristics.�
���������������� C6.1.1.3.� Identify specific program locations where CPI is developed, produced, analyzed, tested, maintained, transported, stored, or used in training.
���������������� C6.1.1.4.� Identify the foreign collection threat to the program.� (MDCI CI Threat Assessments are discussed in C7.� Chapter 7.)
���������������� C6.1.1.5.� Identify program vulnerabilities to specific threats at specific times and locations during all phases of the acquisition cycle.
���������������� C6.1.1.6.� Identify time- or event-phased RTP countermeasures to be employed by the PM to reduce, control, or eliminate specific vulnerabilities to the program to ensure a minimum level of protection for CPI.�
���������������� C6.1.1.7.� Identify anti-tamper (AT) techniques (see C15.� Chapter 15) and system security engineering (SSE) techniques (see C12.� Chapter 12) required to protect CPI.� Ensure these AT and SSE techniques are placed into the system�s design specifications, subsequent technical drawings, test plans, and other program documentation.�
���������������� C6.1.1.8.� Identify elements that require classification and determine the duration of such controls.� The resulting program Security Classification Guide shall be issued by the program�s Original Classification Authority (OCA).
���������������� C6.1.1.9.� Identify protection costs associated with personnel, products, services, equipment, contracts, facilities, or other areas that are part of program protection planning, countermeasures, or program security surveys.� These costs shall be reflected in the Planning, Programming and Budget System.
���������������� C6.1.1.10.� Identify the risks and benefits of developing, producing, or selling the system to a foreign interest, as well as the methods used to protect CRT and/or CPI if such an arrangement is authorized, and whether an export variant is necessary (see C8.� Chapter 8).
���������������� C6.1.1.11.� Identify contractual actions required to ensure that planned systems security engineering, AT techniques, information assurance, information superiority, and/or RTP countermeasures are appropriately applied by defense contractors at contractor locations (see C9 and 17.� Chapter 9 and 17).
���������������� C6.1.1.12.� Coordinate with PMs of supporting programs to ensure that measures taken to protect CRT and/or CPI are maintained at an equivalent level throughout DoD.
������� C6.1.2.� After completing the protection planning process, the PM must, with the assistance of applicable CI and security support activities, ensure implementation of countermeasures to protect the CRT and/or CPI at each location and activity identified in the protection planning process.�
������� C6.1.3.� Protection planning process is continuous and amenable to revision as appropriate.
C6.2.� CRITICAL PROGRAM INFORMATION (CPI)
������� C6.2.1.� CPI is the foundation upon which all protection planning for the program is based, and the reason all countermeasures are implemented.� As an example, the system characteristic might be the small radar cross section.� The CPI are those unique program elements that make the system radar cross-section possible.
������� C6.2.2.� CPI may include components; engineering, design, or manufacturing processes; technologies; system capabilities and vulnerabilities; and other information that give the system its distinctive operational capability.
������� C6.2.3.� To develop the list of CPI, a WIPT will perform a �functional decomposition� of the program or system, as follows:�
���������������� C6.2.3.1.� Analyze the program or system description and those specific components or attributes that give the system its unique operational capability.�
���������������� C6.2.3.2.� Perform the analysis on each subcomponent until a specific element is associated with each system capability.
���������������� C6.2.3.3.� When a component is isolated, evaluate its potential as CPI by applying the following questions:
���������������������������� C6.2.3.3.1.� If a foreign interest obtained this item or information, could a method be developed to degrade system combat effectiveness?
���������������������������� C6.2.3.3.2.� If a foreign interest obtained this item or information, could it compromise the U.S. program or system capabilities?
���������������������������� C6.2.3.3.3.� If a foreign interest obtained this item or information, would it shorten the expected combat-effective life of the system or significantly alter program direction?
���������������������������� C6.2.3.3.4.� If a foreign interest obtained this item or information, would additional RDT&E resources be required to develop a new generation of the U.S. system that was compromised?
���������������� C6.2.3.4.� When CRT are inherited from a technology project and incorporated into an acquisition program, the CRT will be identified as program CPI.
���������������� C6.2.3.5.� An affirmative answer to any of those questions will qualify the item as CPI.
������� C6.2.4.� In addition to the elements organic to the system, the PM should consider any engineering process, fabrication technique, diagnostic equipment, simulator, or other support equipment associated with the system for identification as a possible CPI.� Special emphasis should be placed on any process that is unique to the system being developed.� The PM and program engineer should evaluate each area and identify any activity distinctive to the U. S. industrial and technological base that limits the ability of a foreign interest to reproduce or counter the system.
������� C6.2.5.� Once all system CPI has been identified, additional refinement may be necessary.� Key considerations in this refinement are as follows:
���������������� C6.2.5.1.� Describe CPI in terms understandable by those not in the scientific or engineering field (e.g., use terms from the MCTL (reference (ff)) or National Disclosure Policy (reference (gg))).� The fact that a particular technology is on a technology control list does not mean that technology is a CPI.
���������������� C6.2.5.2.� Provide specific criteria for determining whether CPI has been compromised.
���������������� C6.2.5.3.� Indicate any CPI related to a treaty-limited item.
���������������� C6.2.5.4.� Indicate if this CPI is being or may be used by any other acquisition program or system.
���������������� C6.2.5.5.� Prioritize CPI to ensure that the most important information is emphasized during protection cost analysis.� That process addresses the following two questions:�
���������������������������� C6.2.5.5.1.� What is the extent to which the CPI could benefit a foreign interest?
���������������������������� C6.2.5.5.2.� How difficult is it for a foreign interest to exploit the information?
������� C6.2.6.� CI and security support activities and program protection staff elements will assist the PM in completing this task.�
C6.3.� COORDINATION
������� C6.3.1.� The PM is responsible for developing, approving, and implementing a program protection plan (PPP), which is normally accomplished through a WIPT.� The PM may establish a security WIPT or include the appropriate personnel on an existing WIPT to assist in the preparation of the PPP and supporting documentation.
���������������� C6.3.1.1.� The following personnel or organizational representatives will be represented in the WIPT:
���������������������������� C6.3.1.1.1.� Program office engineering and/or technical staff
���������������������������� C6.3.1.1.2.� Organizational or command security manager
���������������������������� C6.3.1.1.3.� Counterintelligence
���������������������������� C6.3.1.1.4.� Intelligence
���������������������������� C6.3.1.1.5.� Operations security
���������������������������� C6.3.1.1.6.� Foreign disclosure
���������������������������� C6.3.1.1.7.� Base, installation, or post physical security staff
���������������������������� C6.3.1.1.8.� Organization RTP staff representative
���������������������������� C6.3.1.1.9.� Information assurance officer and/or information systems security manager
���������������� C6.3.1.2.� The PM should ensure close coordination and cooperation between the security, foreign disclosure, intelligence, operations security, CI, physical security, and RTP offices and the program office staff during development of a PPP.
������� C6.3.2.� The PM shall identify and prioritize CRT and/or CPI for any component, subsystem, technology demonstrator, or other independent research program that will be incorporated into the PM�s program.� Additionally, the PM of the program using that technology shall ensure such CPI is addressed in the subsystem PPP; subsystem programs with CPI shall ensure that their CPI is included in the major program PPP.
���������������� C6.3.2.1.� The PM shall ensure that CPI from a subsystem is protected to at least an equivalent level.
���������������� C6.3.2.2.� A PM of a system that incorporates a subsystem that has not been reviewed to identify CPI shall request the subsystem program office to review their program for CPI and supply the resulting information and/or documentation.� When supporting activities defined as acquisition programs have not developed a PPP to protect their CPI, the PM incorporating the technology in question must request the subsystem PM to develop and provide an approved PPP.
������� C6.3.3.� The purpose of these coordination activities is to focus on the CPI, and thus minimize costs and administrative burdens, avoid duplication of effort, and ensure effective implementation of the PPP.
������� C6.3.4.� Protection measures should be revised by the DoD Component when a shortcoming exists in the PPP.
������� C6.3.5.� PMs will determine the extent to which there may be foreign involvement in the program (e.g. cooperative development), foreign access to the system and related information during the life of the system (e.g. foreign sales, follow-on support, exchange programs), identify the risks involved, and propose foreign disclosure guidance accordingly.�
C6.4.� PROGRAM PROTECTION PLAN (PPP)
������� C6.4.1.� The PPP serves as the single source document used to coordinate and integrate all protection efforts designed to deny CPI access to anyone not authorized or not having a need-to-know and prevent its inadvertent disclosure to foreign interests.� If there is to be foreign involvement in any aspect of the program, or foreign access to the system to be developed and related information, the PPP must contain provisions to deny inadvertent or unauthorized access by foreign interests.�
���������������� C6.4.1.1.� A PPP should be initiated as early as possible in the Pre-Systems Acquisition phase.
���������������� C6.4.1.2.� The PPP for an acquisition program should be established and approved by the PM as soon as practicable after validation of the Mission Needs Statement or Operational Requirements Document and the determination made that CPI exist.
������� C6.4.2.� Preparation and implementation of a PPP is based on effective application of risk management methodology, not risk avoidance.� Costs associated with protecting CPI should be a balance between protection costs and potential impact, if compromised.� In some cases, residual risks may have to be assumed by the program; such decisions rest with the MDA, based upon the recommendation by the PM.
������� C6.4.3.� When a PPP is required, the following sections describe the process that may be used to prepare the PPP.
���������������� C6.4.3.1.� Any program, product, technology demonstrator, or other item developed as part of a separate acquisition process as a component, subsystem, or modification of the program shall publish a PPP.
���������������� C6.4.3.2.� Effectiveness of the PPP is highly dependent upon the quality and currency of information available to the program office.
���������������������������� C6.4.3.2.1.� Coordination between the program office and CI and security supporting activities is critical to ensure that any changes in the system CPI, threat, or environmental conditions are communicated to the proper organizations.
���������������������������� C6.4.3.2.2.� Intelligence and CI organizations supporting the program protection effort will provide timely notification to the PM of any information on adverse foreign interests targeting their CPI without waiting for a periodic production request.
������� C6.4.4.� The PPP will be classified according to its content.�
������� C6.4.5.� The degree of PPP detail should be limited to that information essential to plan and program for the protection of the CPI, and to provide an executable plan for implementing the required countermeasures throughout the pre-acquisition and acquisition phases.
����� C6.4.6.� While there is no specific format for PPPs, they will include the following items:
���������� C6.4.6.1.� System and program description.
���������� C6.4.6.2.� All program and support points of contact (POCs).
���������� C6.4.6.3.� A prioritized list of program CPI.
���������� C6.4.6.4.� MDCI threat assessment to CPI.
���������� C6.4.6.5.� Vulnerabilities of CPI.
���������� C6.4.6.6.� All RTP countermeasures (e.g., AT techniques, SSE) and Militarily Critical Technology List (MCTL) citations for applicable CRT or CPI.
���������� C6.4.6.7.� All RTP associated costs, to include PPP development and execution, by Fiscal Year.
���������� C6.4.6.8.� CI support plan (CISP).
���������� C6.4.6.9.� Current SCG.
���������� C6.4.6.10.� Foreign disclosure, direct commercial sales, co-production, import, export or demeaned export license requirements, and/or TA/CP.
���������� C6.4.6.11.� Delegation of Disclosure Authority Letter, if appropriate.
������� C6.4.7.� Specific guidance on topics to be addressed in a PPP is provided in sections C6.5. through C6.10., and in C7., C8., C9., and C10. Chapters 7, 8, 9, and 10.�
C6.5.� SYSTEM AND PROGRAM DESCRIPTIONS
�������
������� C6.5.1.� System Description.� Since most acquisition programs combine existing, proven technology, as well as information with state-of-the-art technology, the system description included in a PPP should provide the reviewer with a clear indication of the capabilities and limitations of the system being acquired, including simulators and other supporting equipment.� The purpose of the system description is to set the stage for identifying CPI.� The system description should be based on the approved MNS or ORD.
���������������� C6.5.1.1.� Anticipated employment of the system, along with the strategic, operational, or tactical impact of the system, within the battlespace.
���������������� C6.5.1.2.� Specific characteristics that distinguish the system from existing systems, other systems under development, or that provide the system with unique operational or performance capability.
������� C6.5.2.� Program Description.� This section should be a short summary of the organization and structure of the office responsible for developing and fielding the acquisition system.� Early in the acquisition process, that information may be somewhat limited.� Detail should be added as the structure and participants in the program are identified and as their role in program protection activities becomes known.� The program description should briefly describe the following:
���������������� C6.5.2.1.� The program management chain of command, including the Program Executive Officer, Service Acquisition Executive, and/or MDA for the program and supporting programs.
���������������� C6.5.2.2.� The locations, points of contact (POCs), and telephone numbers of prime contractors, sub-contractors, vendors, DoD sites, Federal agencies, Government Owned - Contractor Operated and DoD RDT&E activities and/or facilities that will handle, store, or analyze CPI-related material.
C6.6.� FOREIGN COLLECTION THREAT
������� C6.6.1.� Foreign collection threat assessment used by the program office in planning protection for the CPI should be based upon a National-level intelligence estimate known as a �MDCI threat assessment.�
���������������� C6.6.1.1.� The MDCI threat assessment is prepared and produced as a stand-alone document by the applicable DoD CI analysis center (see C7.� Chapter 7).
���������������� C6.6.1.2.� The MDCI threat assessment should not be confused with a system threat assessment (STA).� The MDCI analysis identifies foreign interests having a collection requirement and capability to gather information about the system being developed.�
���������������� C6.6.1.3.� Sudden changes in the operational threat should be reviewed as they occur to determine if the changes are due to successful foreign intelligence collection.
���������������� C6.6.1.4.� The PM and WIPT should compare results of the MDCI threat assessment with the CPI and vulnerabilities to determine the level of risk to the program.
���������������� C6.6.1.5.� The WIPT should integrate environmental factors and arms control-related issues that might reduce the ability of foreign interests to collect information at a given location in the MDCI threat assessment, where applicable.
������� C6.6.2.� A threat exists when:� a foreign interest has a confirmed or assessed requirement for acquiring specific classified or sensitive defense information or proprietary or intellectual property information; a foreign interest has the capability to acquire such information; and/or the acquisition of such information by the foreign interest would be detrimental to U.S. interests.�
������� C6.6.3.� Confirmed or assessed identification of foreign collection requirements will provide indications of probable sources and methods that might be employed to satisfy a collection requirement.
������� C6.6.4.� The applicable CI and security support activities should assist the program office in preparing collection requirements and production requests to the applicable DoD Component intelligence or CI analysis center.�
���������������� C6.6.4.1.� CI and security support activities should expedite the request to the intelligence center that will normally support the PM.
���������������� C6.6.4.2.� An informational copy should be sent to the intelligence analysis center of any other DoD Component involved in the program to facilitate a single and unified position on the collection threat.� JCAG will be provided a copy upon publication.
C6.7.� VULNERABILITIES
������� C6.7.1.� A vulnerability is the susceptibility of a program to a threat in a given environment.
������� C6.7.2.� Vulnerabilities to the program�s CPI should be based upon one or more of the following:
���������������� C6.7.2.1.� How CPI is stored, maintained, or transmitted (e.g., electronic media, blueprints, training materials, facsimile, modem)?
���������������� C6.7.2.2.� How CPI is used during the acquisition program (e.g., bench testing, field testing)?
���������������� C6.7.2.3.� What emanations, exploitable signals, or signatures (electronic or acoustic) are generated or revealed by the CPI (e.g., telemetry, acoustic energy, radiant energy)?
���������������� C6.7.2.4.� Where CPI is located (e.g., program office, test site, contractor, academia, vendor)?
���������������� C6.7.2.5.� What types of OPSEC indicators or observables are generated by program or system functions, actions, and operations involving CPI?
���������������� C6.7.2.6.� What conferences, symposia, or foreign travel are the PM and PM staff members participating in or planned to be involved in?
���������������� C6.7.2.7.� What level of human intelligence or insider threat is evident or projected at the PM location or other locations where CPI will be located?
���������������� C6.7.2.8.� What foreign disclosures are planned, proposed, or staffed for formal release?
���������������� C6.7.2.9.� What degree of foreign participation is currently pursued or being planned for the program or locations where CPI will be located?
������� C6.7.3.� Identified vulnerabilities will be prioritized by the PM.
���������������� C6.7.3.1.� Prioritization should be based upon the consequences if CPI is lost or compromised, and the level of difficulty for a foreign interest to exploit the information.�
���������������� C6.7.3.2.� Factors to be considered include the adverse impact on the combat effectiveness of the system, the effect on the combat-effective lifetime, and the cost associated with any modifications required to compensate for the loss.
C6.8.� RTP COUNTERMEASURES
������� These are measures employed to eliminate or reduce the vulnerability of CPI to loss or compromise, and include any method (e.g., AT techniques, information assurance) that effectively negates a foreign interest capability to exploit CPI vulnerability.
������� C6.8.1.� RTP countermeasures shall be developed to eliminate vulnerabilities associated with an identified threat to CPI based upon the authoritative, current, and projected threat information in the MDCI threat assessment.� RTP countermeasures shall:
���������������� C6.8.1.1.� Be applied in a time- or event-phased manner.
���������������� C6.8.1.2.� Be implemented until they are no longer required.� They shall be terminated or reduced as soon as practicable after the threat, CPI, or environmental changes lead to a reduction or elimination of the vulnerabilities or negation of the threat.� For example, arms control countermeasures might be implemented only while the facility is vulnerable to an arms control treaty mandated inspection or an overflight by foreign inspectors.
���������������� C6.8.1.3.� Address DoD Information Technology Security Certification and Accreditation Process (DITSCAP) compliance for all information technology systems and/or networks.� (See C17.� Chapter 17.)
������� C6.8.2.� PMs should establish a countermeasures program based upon threat, risk management, OPSEC methodology, and vulnerability assessments.
���������������� C6.8.2.1.� The PM should assess the costs associated with applicable countermeasure application or implementation and compare them to the risk associated with loss or compromise of the CPI.�
���������������� C6.8.2.2.� The PM should provide justification in the countermeasures section of the PPP whenever countermeasures are not developed to reduce, control, or eliminate a CPI vulnerability.
������� C6.8.3.� If the acquisition program does not have an assigned or contracted security organization, applicable CI and security support activities should assist the program office in developing a draft countermeasures concept based upon the PM�s guidance.� The PM should designate an element of the program office as responsible for publishing a PPP.
������� C6.8.4.� Countermeasures recommended to eliminate or reduce vulnerabilities associated with CPI, at government and contractor facilities, may not be waived while the affected facilities are vulnerable to arms control treaty inspections or overflights by foreign interests.
������� C6.8.5.� The requirement for contractor compliance with the government-approved PPP must be included in the government�s solicitation and resulting contracts (see C9.� Chapter 9).�
������� C6.8.6.� Training in protection of research and technology information and security awareness are integral parts of the countermeasures effort.
���������������� C6.8.6.1.� Following approval of the PPP, the PM should implement a training program to inform all program members of the requirements in the PPP.
���������������� C6.8.6.2.� Emphasis should be placed on encrypting the transmission of electronic messages, facsimile transmissions, and telephone transmissions relating to CPI, underpinning technologies, and other CUI related to programs containing CRT or CPI.� These transmissions should be via Federal Information Processing Standard 140-2 (reference (hh)) compliant encryption.
������� C6.8.7.� Countermeasures are dynamic.� As the threat, CPI, or environment changes, the countermeasures may also change.� The PM should update the PPP as system vulnerabilities change and thus reduce the cost and administrative burden on their programs.
C6.9.� SECURITY CLASSIFICATION GUIDES
������� C6.9.1.� When necessary, each acquisition will develop a SCG in accordance with DoD 5200.1-R (reference (c)).�
������� C6.9.2.� The SCG will address each CPI, as well as other relevant elements of information requiring protection.� Additionally, the SCG will address all controlled unclassified information.�
������� C6.9.3.� All controlled unclassified information, �FOUO� as defined in DoD 5400.7-R (reference (p)), or information with other approved markings that require dissemination controls (e.g., DoD Directive 5230.24 and DoD Directive 5230.25 (references (cc) and (dd))), is exempt from mandatory disclosure under the Freedom of Information Act and will be identified in the SCG.
������� C6.9.4.� The SCG will be reviewed, and amended when necessary, as part of each milestone review or as otherwise required by DoD 5200.1-R (reference (c)).
C6.10.� PROTECTION COSTS
������� C6.10.1.� Cost data associated with countermeasures and other RTP efforts shall be compiled by the WIPT, tabulated by acquisition phase, and included in the PPP.� Cost accounting should only address the costs specific to the implementation of the PPP and exclude projected costs for operating with classified information.� (See C10.� Chapter 10.)
������� C6.10.2.� Costs should be displayed by security discipline (e.g., physical security, personnel security, industrial security) and category (e.g., equipment, services, personnel).
������� C6.10.3.� Cost data for each phase should be as specific as possible.� Additionally, actual annual costs for the previous phase should be compiled and compared with the projected annual cost for the current acquisition phase.� Significant deltas showing differences between projected and actual cost data should be explained.� This information should be used for justifications required by the Planning, Programming, and Budget System.
������� C6.10.4.� The Acquisition Program Baseline (APB) should include costs related to PPP implementation.
C7. CHAPTER 7
MULTIDISCIPLINE CI THREAT ASSESSMENT
C7.1.� GENERAL
������� C7.1.1.� When an acquisition program containing CPI is initiated, the PM should request a MDCI threat assessment from the servicing CI organization.�
������� C7.1.2.� CI organizations will need information that describes the CPI and its projected use to determine the foreign collection threat to an acquisition program.
������� C7.1.3.� At a minimum, an MDCI threat assessment will include an evaluation of foreign collection threats to specific program or project technologies, the impact if that technology is compromised, and identification of related foreign technologies that could impact program or project success.
������� C7.1.4.� An MDCI threat assessment will be updated once every two years throughout the acquisition process.� Any changes will be briefed to the program or project manager within 60 days.
������� C7.1.5.� When gathering information to meet the needs described in this Regulation, intelligence and CI organizations must comply with DoD Directive 5240.1 and DoD 5240.1-R (references (q) and (r)).� Information gathered by non-intelligence community entities must comply with DoD Directive 5200.27 (reference (ii)).
C7.2.� THREAT ANALYSIS
������� C7.2.1.� The request to the CI organization for the threat assessment should contain the following information and be classified as appropriate.
������� C7.2.1.1.� Program office, designator, and address.
������� C7.2.1.2.� PM�s name and telephone number.
������� C7.2.1.3.� POC�s name, address, and telephone number.
������� C7.2.1.4.� Supporting or supported programs� or projects� names and locations.
������� C7.2.1.5.� Operational employment role, if any.
������� C7.2.1.6.� List of CPI.
������� C7.2.1.7.� Relationship to key technologies or other controlled technology lists of the Departments of Defense, Commerce, and/or State.
������� C7.2.1.8.� CPI technical description, including distinguishing characteristics (e.g., emissions; sight or sensor sensitivities) and methods of CPI transmittal, usage, storage, and testing.
������� C7.2.1.9.� Use of foreign equipment or technology during testing (if known).
������� C7.2.1.10.� Anticipated foreign involvement in the development, testing, or production of the system.
������� C7.2.1.11.� Contractor names, locations, POCs, and telephone numbers, as well as the identification of each CPI used at each location.
�������
������� C7.2.1.12.� Reports of known or suspected compromise of CPI.
������� C7.2.2.� After the request is submitted, the Component CI organization should provide a preliminary MDCI threat assessment to the program office within 90 days.� A preliminary assessment may be more generic and less detailed than the final assessment.
���������������� C7.2.2.1.� The preliminary assessment will be limited in use since it only provides an indication of which countries have the capability to collect intelligence on the system or technology as well as the possible interest and/or intention to collect it.
���������������� C7.2.2.2.� The preliminary MDCI assessment may serve as the basis for the draft PPP.
���������������� C7.2.2.3.� A draft PPP should be submitted for approval only after the final MDCI threat assessment has been received from the applicable DoD Component CI and/or intelligence support activity.�
������� C7.2.3.� The MDCI threat assessment should be returned to the requesting program office.� The goal is to return the final MDCI threat assessment to the PM within 180 days of receiving the request by the CI and/or intelligence organization.
������� C7.2.4.� At a minimum, the MDCI threat assessment should answer the following questions about CPI.
���������������� C7.2.4.1.� Which foreign interests might be targeting the CPI and why?
���������������� C7.2.4.2.� What capabilities does each foreign interest have to collect information on the CPI at each location identified by the program office?
���������������� C7.2.4.3.� Does evidence exist to indicate that a program CPI has been targeted?
���������������� C7.2.4.4.� Has any CPI been compromised?
C8. CHAPTER 8
TECHNOLOGY ASSESSMENT / CONTROL PLAN (TA/CP)
C8.1.� GENERAL
������� C8.1.1.� This Chapter supplements the policy in DoD Directive 5530.3 (reference (m)) and is not designed to replace nor supersede that Directive.� During a conflict in policy between this chapter and reference (m), the policy prescribed in reference (m) shall apply.
������� C8.1.2.� The TA/CP, or similar document, should be a part of the PPP for all acquisition programs with international involvement.
������� C8.1.3.� The TA/CP must be included in the PPP, when it is determined that there is likely to be foreign involvement in the development program or there will be foreign access to the resulting system or related CRT or CPI by virtue of foreign sales, co-production, follow-on support, exchange program, training, or multinational exercises or operations.� Much of the information required for the preparation of the TA/CP can be obtained from the MNS, the Analysis of Alternatives (AOA), the Critical Requirements Document (CRD), the ORD, the Cooperative Opportunities Document (COD), and the justification and supporting information used in preparing those documents.
C8.2.� PURPOSE
������� The TA/CP should be used to do the following:
������� C8.2.1.� Assess the feasibility of U. S. participation in joint programs from a foreign disclosure and technical security perspective.
������� C8.2.2.� Prepare guidance for negotiating the transfer of classified information and critical technologies involved in international agreements.
������� C8.2.3.� Identify security arrangements for international programs.
������� C8.2.4.� Provide a basis for the DDL that contains specific guidance on proposed disclosures.
������� C8.2.5.� Support the acquisition decision review process.
������� C8.2.6.� Support decisions on foreign sales, co-production or licensed production, commercial sales of the system, or international cooperative agreements involving U.S. technology or processes.
������� C8.2.7.� Support decisions on the extent and timing of foreign involvement in the program, foreign sales, and access to program information by foreign interests.
������� C8.2.8.� When it is determined there likely will be foreign involvement in the program, or foreign access to the resulting system or related information it is advantageous to prepare the TA/CP after completing the identification of CRT, CPI, and the classification guidance.� The TA/CP analysis will often assist in developing vulnerabilities and proposed RTP countermeasures.� Polices governing the foreign disclosure of intelligence information are in Director of Central Intelligence Directives (DCIDs) 1/7 and 5/6 (references (jj) and (kk)), information security products and information in National Security Telecommunications and Information Systems Security (NSTISS) Policy Number 8 (reference (ll)), and nuclear information governed by the Atomic Energy Act (reference (mm)).� These documents must be consulted when these types of information are involved in an acquisition program.
C8.3.� CONTENT
������� The TA/CP is composed of four sections; the �Program Concept,� the �Nature and Scope of the Effort and the Objectives,� the �Technology Assessment,� and the �Control Plan.�� Those TA/CP subsections are the basis for preparing the DDL.
������� C8.3.1.� Program Concept.� This section requires a concise description of the purpose of the acquisition program.� It should describe, in the fewest words possible, the purpose of the system and the system threat or the military or technical requirements that created the need for the system.� The description must be consistent with the PPP.
������� C8.3.2.� Nature and Scope of Effort and the Objectives.� This section briefly explains the operational and technical objectives of the program (e.g., co-production, cooperative research and development) and discusses any foreign participation or involvement.� If foreign participation or involvement or the release of information to support potential foreign sales is considered likely, the phasing and disclosures at each phase should be described briefly.� The POC for all aspects of the TA/CP must be identified, including address, telephone numbers, and facsimile numbers.
������� C8.3.3.� Technology Assessment.� The third section is the most important part of the TA/CP.� It analyzes the technology involved in the program, its value, and the consequences of its compromise, and describes conclusions regarding the need for protective security measures; the advantages and disadvantages of any foreign participation in the program, in whole or in part; and foreign sales.� That assessment must be specific concerning the phased release of classified and unclassified information that supports potential foreign involvement and foreign sales.� Since preparation of this section requires a joint effort involving program management, security, intelligence, and foreign disclosure personnel, it may be a task for the WIPT.
���������������� C8.3.3.1.� When the TA/CP is prepared in the early stage of program protection planning, emphasis will be placed on describing the value of the technology and systems in terms of military capability; economic competitiveness of the U.S. industrial base and technology; susceptibility to compromise; foreign availability; and likely damage in the event of compromise.
���������������� C8.3.3.2.� In all cases, this analysis must result in a conclusion on whether a cooperative program, co-production, or foreign sale will result in clearly defined operational or technological benefits to the United States that are expected to outweigh any damage that might occur if there should be a compromise or unauthorized transfer.� Specific reasons must be provided.�
���������������� C8.3.3.3.� The assessment must identify and explain any critical capability, information, or technology that must be protected.� It may reveal that an adjustment to program phasing is necessary so critical information is released only when absolutely needed.� It should identify any CPI that may not be released due to the impact on the system�s combat effectiveness.� Additionally, it will identify the need for special security requirements to be adopted such as a program-specific security plan to govern international involvement.� Finally, the assessment must evaluate the risk of compromise, based on the capability and intent of foreign participants or purchasers to protect the information, and the susceptibility of the system to compromise if not protected.�
���������������� C8.3.3.4.� The assessment must also discuss any known foreign availability of the information, system, or technology involved; previous release of the same or similar information, system, or technology to other countries; and, when foreign involvement or sales are recommended, its release to other participants.
������� C8.3.4.� Control Plan.� The fourth section, together with the technology assessment, provides the basis for guidance on negotiating technical and security aspects of the program, and development of disclosure guidelines for subsequent sales and foreign participation in the program.
���������������� C8.3.4.1.� The Control Plan must describe actions that are to be taken to protect U.S. interests when foreign involvement or sales are anticipated.� Those actions must be specific and address specific risks, if any, as discussed in the technology assessment.� Actions might include withholding certain information, stringent phasing of releases, or development of special security requirements.
���������������� C8.3.4.2.� The plan should also identify any design or engineering changes that may be necessary or desirable to ensure the protection of CPI.
���������������� C8.3.4.3. The plan should describe how security provisions of an agreement and/or applicable regulations are to be applied to the specific program, agreement, or sale.
���������������� C8.3.4.4. In preparation of the Control Plan, special consideration must be given to the export restrictions on sensitive technologies and materials amplified in DoD Instruction S-5230.28 and the National Information Disclosure Policy Committee Policy Statement, �Foreign Release of Low Observable and Counter Low Observable Information and Capabilities (U)� (references (nn) and (oo)).
������� C8.3.5.� DDL.� The PM must prepare a DDL as part of a recommendation for foreign involvement, disclosure of the program to foreign interests, request for authority to conclude an international agreement, or a decision to authorize foreign sales.
���������������� C8.3.5.1.� The DDL should provide detailed guidance on releasability of all elements of the system, to include its technology and associated information.�
���������������� C8.3.5.2.� Until the DDL has been approved by both the originating authority and the Office of the USD(P), there should be no promise to release or actual release of sensitive information or technology.
���������������� C8.3.5.3.� The DDL shall be developed by the PM, who along with the applicable designated disclosure authority shall agree on its content.� The DDL is provided to the MDA for approval and at each subsequent milestone review.� The PM shall use DoD Directive 5230.11 (reference (k)) in the preparation of a DDL.
C9. CHAPTER 9
CONTRACTING AND RESOURCES
C9.1.� EARLY COORDINATION�
������� As discussed in C5.� Chapter 5, RTP should be a subject for early coordination by program management and contracting personnel to ensure that contractual documents contain the applicable protection requirements.� Early coordination is essential to having adequate coverage in contractual documents and thus avoids additional and unnecessary costs due to late application of RTP requirements.� The expected range of protection requirements and projected resources required should be estimated to ensure research and acquisition planning documents address RTP.�
C9.2.� PRE-CONTRACT AWARD�
The pre-award phase includes pre-solicitation, solicitation, source selection evaluation, and other pre-award activities.�
������� C9.2.1.� Acquisition organizations generally have local instructions and related checklists to aid the program management staff in completing the actions necessary to arrive at a legal and successful contract.� Such instructions and checklists should be written to address program protection activities and requirements.�
������� C9.2.2.� Program protection requirements must be defined early enough to be included in the draft request for proposal (RFP) and the RFP.
���������������� C9.2.2.1.� The initial program management staff, with the assistance of the program protection POC, will provide the responsible contracting office with information that describes the nature and extent of program protection requirements that must apply to the contemplated contract and estimates for the resources necessary to contractually execute the program.� See the information listed in subsection C6.4.6.�
���������������� C9.2.2.2.� Program protection information developed will be used to prepare the program protection section for inclusion in the RFP.� A repetitive process may be necessary to complete the RFP, with a final review of the RFP occurring prior to release to industry.� Ensure that the appropriate Federal Acquisition Regulation (FAR) and/or Defense Federal Acquisition Regulation Supplement (DFARS) clauses have been activated for RTP (e.g., DFARS (35,013) 242.402) (reference (pp)).
������� C9.2.3.� Once the proposals are received in response to the RFP, they will be evaluated using specified source selection criteria.� The resulting evaluation should address the proposed ways of satisfying program protection requirements.� The evaluation should also consider the cost to execute each of the proposed approaches to satisfy the contractor portion of the PPP.� The PM should have an RTP specialist on the source selection committee.
������� C9.2.4.� Approaches in the selected contractor�s proposal documents must be incorporated into the contract before award.� Action must be taken to ensure that the RTP provisions in the proposal are fully implemented by the prime contract.�
C9.3.� POST CONTRACT AWARD
������� C9.3.1.� It is not unusual for contract modifications to be made reflecting fiscal or other program changes.� As with the pre-award actions, the organization�s RTP representative must continue to work with the program management staff and the contracting officer if RTP changes are required.�
������� C9.3.2.� Post award meetings are conducted to identify and highlight specific items of interest that are pertinent to contract execution.� The government�s interest and expectations regarding the contractor�s compliance with the contract�s RTP requirements should be emphasized in this forum.�
������� C9.3.3.� A primary post award activity is �baselining� the contract.� RTP actions must be addressed in this activity and, if applicable, identified as a reportable item in the baseline.� When used, the contractor�s program protection implementation plan (PPIP) will form a principal source for the contract RTP baseline.
������� C9.3.4.� The contracting officer�s representative (COR) is formally identified during the post award activities and becomes the focal point, along with the PM, for administering contract requirements, including RTP.� The COR and the PM need to understand RTP is important to successful achievement of the program cost, schedule, and performance objectives.�
C9.4.� CONTRACTOR PERFORMANCE MONITORING
������� C9.4.1.� The COR, along with the PM and contracting officer (CO), continue to be important in ensuring that RTP requirements are accomplished, particularly if there are any modifications to the contract.� The RTP POC should monitor performance and schedule of RTP activities.� As part of the PM staff, the RTP POC should work through the PM, COR, and CO in accomplishing RTP goals.�
������� C9.4.2.� Planning for performance monitoring begins with RFP activities, pre-award issues, and continues with the contract baselining and any necessary re-baselining.
������� C9.4.3.� The contract baseline, once documented, will be the prime contractor performance measurement tool.� That baseline will be compared with periodic performance reports which address work accomplished and may address costs incurred and task funding.� When the work breakdown structure is developed, any RTP action identified in the statement of work, preliminary acquisition planning activities, or the RFP should be considered for identification as a �reportable item.�
C9.5.� CONTRACTOR COSTS�
To properly support contract activities, RTP costs must be identified as part of the initial program definition and structuring.� The cost estimates are then used in the early contract development process, starting with drafting of the RFP.
������� C9.5.1.� Cost estimates should be identified by category (i.e., personnel, products, services, equipment) to include any information systems requirements.�
������� C9.5.2.� Within each category of RTP costs, the items should be further identified by security discipline.
������� C9.5.3.� Costs for implementing industrial security are included in the overhead portion of contractor costs.� DoD security countermeasures are typically included in level-of-effort costs for DoD agencies.� These costs should not be included in the PPP since they are not additive costs to the acquisition program.� The baseline for standard security actions should be determined before determining program-specific RTP costs.
������� C9.5.4.� All RTP costs for implementing the foreign disclosures and/or national disclosure policies shall be identified by category in accordance with paragraphs C9.5.1 through C9.5.2.
C9.6.� PROVIDING DOCUMENTATION TO CONTRACTORS
������� C9.6.1.� The PM, in coordination with the RTP POC and the contracting officer, must determine when prime contractors, and subcontractors supporting the RTP effort, need access to CPI documentation.
������� C9.6.2.� When a contractor is to be granted access to sensitive information, controlled unclassified information, For Official Use Only, export controlled or unclassified technical data the contract will provide authorization for access to contractor facilities by the responsible government industrial security office (DSS or the Service cognizant security authority).� That authorization is necessary to permit surveys, inspections, advice or assistance visits, or inquiries, which are necessary to ensure protection of the sensitive information and implementation of RTP activities at prime, subcontractor, and/or vendor facilities.
������� C9.6.3.� When possible, applicable threat information (i.e., MDCI threat assessment) should be shared with cognizant contractor Facility Security Officer to ensure their understanding of the threat.
C9.7.� SUPPORT FROM COGNIZANT GOVERNMENT
INDUSTRIAL SECURITY OFFICES
The contract�s DD Form 254, �DoD Contract Security Classification Specification,� should specifically identify RTP assessments and reviews to be conducted by the responsible government industrial security office (e.g., DSS).� Organizations conducting those reviews should:
������� C9.7.1.� Conduct or participate in reviews and assistance visits at contractor facilities and contractor activities at government facilities.� Reviews at contractor facilities in the United States assess compliance with contractually-imposed RTP measures, when contract provisions authorize such reviews and visits.
������� C9.7.2.� Disseminate evaluation reports to appropriate acquisition program officials (e.g., Program Executive Officers (PEOs), PMs, user organization officials).� Unless specifically prohibited, the PM should provide reports to appropriate contractor personnel.�
C10. CHAPTER 10
RTP COSTING AND BUDGETING
C10.1.� GENERAL
���������� C10.1.1.� Ultimately, the success of an acquisition program will depend on protecting the research and technology upon which the acquisition is based.� Integral to this is understanding and applying a costing methodology to ensure the validated RTP countermeasures are funded and implemented.
���������� C10.1.2.� RTP requirements should be incorporated into initial program funding and subsequent budget submissions to secure the investment of DoD RDT&E resources (funds; people�from the scientist to the warfighter; and time) that are committed at program onset.� If this is not achieved, additional resources will be required later to overcome compromise of program technology and result in untimely delays in providing necessary systems to the warfighter while additional resources are appropriated.
���������� C10.1.3.� When RTP professionals are part of the program costing and budgeting processes, the RTP requirements can be properly addressed during programming and budgeting cycles.
C10.2.� RTP
COSTING
���������� C10.2.1.� Security, counterintelligence and intelligence professionals must be integrated into the program costing process at the earliest opportunity.�
���������� C10.2.2.� Program resource managers are responsible for developing work breakdown structures (WBS) and Cost Analysis Requirements Documents (CARD) as part of the overall costing process.� The CARD is developed in concert with the WBS and serves as the costing portion of the WBS.� Costs for material, personnel/labor, training, etc., are incorporated into a requirements document to define overall RTP costs.
���������� C10.2.3.� A separate WBS category will provide managers with visibility into RTP costs and actual funding available to support the RTP effort.� A separate WBS category is recommended for RTP requirements such as anti-tamper, system security engineering, information assurance, and program protection implementation plan (PPIP).�
C10.3.� RTP
BUDGETING
���������� C10.3.1.� Once RTP cost requirements are properly estimated and documented, the next step in the process is their submission and validation as part of the program budgeting process.
���������� C10.3.2.� All RTP costing requirements must be coordinated with the program resource manager who prepares budget submissions to the PM.
���������� C10.3.3.� Often, a validation board is assembled to review all program costing requirements.� This board validates the cost (verifies the methodology used to project the costs) and prioritizes program cost requirements.� When RTP cost proposals are submitted, RTP professionals should be represented to support these proposals to the validation board.� RTP professionals should serve as advisor to the PM for RTP costs coming from other organizations or from contractors.
���������� C10.3.4.� Once a program�s budget is approved and the RTP requirement funded, a separate RTP funding line item will be provided.� This line is used as an accounting of the funds that are distributed regarding this RTP requirement.
���������� C10.3.5.� RTP professionals who manage funding and/or the implementation of the PPIP are required to annually update their funding requirements and contribute to the overall program budget submission process.� RTP costs will be validated each year.
C11. CHAPTER 11
EXECUTION OF THE PPP
C11.1.� GENERAL
������� C11.1.1.� The acquisition PM has the primary responsibility for PPP execution.� Specific functions and actions may also be assigned to supporting security, CI, and intelligence organizations, as well as supporting acquisition organizations and defense contractors.
������� C11.1.2.� Proper PPP execution depends on allocation of resources for planned RTP countermeasures and communication of the RTP countermeasures plan to applicable contractors, as well as the acquisition, security, CI, and intelligence activities supporting the program.
C11.2.� DISTRIBUTION OF THE PPP
������� C11.2.1.� Once the PPP is approved, the PM must ensure that all activities assigned RTP actions in the PPP receive a copy of the approved plan or those portions pertaining to their tasks.� Organizations that should be considered for PPP distribution include the following:
���������������� C11.2.1.1.� Program contractors having CPI under their control.
���������������� C11.2.1.2.� Responsible government industrial security offices (e.g., DSS offices supporting the program at contractor sites covered by the PPP and/or the PPIP).
���������������� C11.2.1.3.� DoD test ranges and centers applying CPI countermeasures.
���������������� C11.2.1.4.� CI activities supporting program sites having CPI countermeasures applied.
������� C11.2.2.� If the PM decides to limit distribution of the entire PPP, at a minimum, the CPI and RTP countermeasures portions should be distributed to the appropriate organizations.
C11.3.� ASSESSMENT OF PPP EFFECTIVENESS
������� C11.3.1.� The PM, assisted by applicable security and CI activities, should assess PPP effectiveness, and the RTP countermeasures prescribed therein, as part of the normal program review process.� In the past, security surveys have been used to aid the PM in performing these assessments.
������� C11.3.2.� Such assessments should be planned considering the overall program schedule, the time-phased arrival or development of CPI at specific locations, and the schedule to revise the PPP.
C12. CHAPTER 12
SYSTEM SECURITY ENGINEERING
C12.1.� GENERAL
���������� System security engineering (SSE) may be an important element of RTP and the vehicle for integrating RTP into the systems engineering process.� Systems engineering activities intended to prevent and/or delay exploitation of CRT and/or CPI in U.S. defense systems may also include Anti-Tamper (AT) activities (see C15. Chapter 15).� The benefit of SSE is derived after the acquisition by mitigation of security threats against the system during deployment, operations, and support.� SSE also addresses possible capture of the system by the enemy in combat or hostile action.
C12.2.� PURPOSE
���������� C12.2.1.� The System Security Management Plan (SSMP) establishes guidance for the following tasks.
C12.2.1.1.� Analysis of security
design and engineering vulnerabilities.
C12.2.1.2.�
Development of recommendations for engineering changes to eliminate or
mitigate vulnerabilities consistent with other design and operational
considerations.�
���������� C12.2.2.� The SSMP is applicable to acquisition of new (whether off-the-shelf or non-developmental items) or existing systems or equipment.
C12.3.� SYSTEM
SECURITY ENGINEERING PLANNING
���������� C12.3.1.� The System Engineering Management Plan (SEMP) is the top-level management document used to describe the required systems engineering tasks.� The System Security Management Plan (SSMP) is a detailed plan outlining how the SSE manager (SSEM) and the contractors are going to implement SSE and may be part of the SEMP.�
���������� C12.3.2.� MIL-HDBK-1785 (reference (qq)) establishes the formats, contents, and procedures for the SSMP.� Data Item Description (DID), DI-MISC-80839, SSMP, is applicable.�
���������� C12.3.3.� A System Security Engineering Working Group (SSEWG) is comprised of acquisition program office personnel; supporting CI, intelligence, and security personnel; system user representatives; and other concerned parties.� The SSEWG should be formed as early in the acquisition process as possible, but not later than Component Advanced Development phase of the acquisition.� The SSEWG will define and identify all RTP aspects of the system, develop RTP architecture, review the implementation of system architecture, and participate in design validation.� Recommendations and decisions from the SSEWG shall be provided to the PM.
C12.4.� SYSTEM
SECURITY ENGINEERING PROCESS
���������� C12.4.1.� SSE supports the development of programs and design-to-specifications providing life-cycle protection for critical defense resources.� Activities planned to satisfy SSE program objectives are described in the SSMP
���������� C12.4.2.� SSE secures the initial investment by �designing-in� necessary RTP countermeasures and �engineering-out� RTP vulnerabilities and results in saving time and resources over the long term.� During the system�s design phase, SSE should identify, evaluate, and eliminate (or contain) known or potential system vulnerabilities from deployment through demilitarization.
���������� C12.4.3.� The SSE process defines the procedures for contracting for an SSE effort and an SSMP.� Implementation requires contractors to identify operational vulnerabilities and to take action to eliminate or minimize associated risks.
C12.4.4.� Contracting Data Item Descriptions (DIDs) and Contract Data Requirements Lists (CDRLs) may be tailored to the system in order to obtain contractor-produced plans or studies satisfying specific program needs.�
C12.5.� MILITARY HANDBOOK 1785�
���������� C12.5.1.� MIL-HDBK-1785 (reference (qq)) contains the procedures for contracting for an SSE effort and an SSMP.� The format and contents are outlined in the appropriate Data Item Descriptions (DIDs) listed in MIL-HDBK-1785.
���������� C12.5.2.� MIL-HDBK-1785 is in the SCOR and also located on web site http://astimage.daps.dla.mil/docimages/0002/01/88/MIL-HDBK.PD0.� The proponent for the handbook is Commander, Naval Air Systems Command, ATTN:� AIR-7.4.4., 22514 McCoy Road, Unit 10, Patuxent River, MD� 20670-1457.
C12.6.� SECURITY ENGINEERING FOR INTERNATIONAL PROGRAMS
���������� SSE should include an assessment of security criteria that precludes international cooperative programs, direct commercial sales, and/or foreign military sales (FMS) cases.� From this assessment, engineering and software alternatives, such as export variants, that would permit such transactions, should be identified and considered.�
PART IV
PROTECTION ACTIVITES
C13.� CHAPTER 13
SECURITY SUPPORT PLAN
C13.1.� GENERAL
���������� C13.1.1.� A SSP
shall be developed for each RDT&E site when the project or program manager
determines their project or program has CRT.�
(A recommended format for the SSP is
in the Specialized C3I Operating Reference (SCOR).)
���������������� C13.1.1.1.� For RDT&E projects, the SSP, an analogous to the PPP, will be the RDT&E site director�s and/or manager�s integrated, comprehensive, time-phased security plan for the implementation and support of their research efforts.� The SSP will identify and forecast for the specific protection level requirements and security support needed at contractor operated facilities and all DoD RDT&E sites, laboratories, and other locations and define the protective measures required at each location.
C13.2.� PURPOSE
���������� The purpose of the SSP is to provide a tool for execution of planned RTP countermeasures in a single, cost-effective, integrated effort.� As technology transitions and is incorporated into a program, the SSP will be provided to the PM.
C13.3.� PROCESS
���������� C13.3.1.� Security support planning begins when emerging technology is identified as having a military or space application.
���������� C13.3.2.� Scientists, researchers, and laboratory site directors are responsible for the employing the RTP countermeasures for CRT or CPI as soon as they are identified.� CPI may be provided to the RDT&E sites in order that underpinning CRT or new CRT is incorporated into the acquisition program.
���������� C13.3.3.� The SSP will be developed to identify security processes and procedures to protect CRT or CPI from the time or event they are identified.�
���������� C13.3.4.� The SSP will identify and forecast specific security requirements, including those identified in the CISP, and support needed at all RDT&E locations and depot sites as well as contractor-operated facilities.
C14.� CHAPTER 14
COUNTERINTELLIGENCE SUPPORT PLAN
C14.1.� GENERAL
���������� C14.1.1.� A tailored CISP will be developed for every
DoD RDT&E activity and for each DoD acquisition program with identified
CPI.�
���������� C14.1.2.� RDT&E site directors, security managers,
and supporting CI organizations are responsible for developing a CISP for each
RDT&E facility.
���������� C14.1.3.� PMs and their supporting security and CI
organizations are responsible for developing a CISP for each acquisition
program with CPI.� The CPI will be
listed in priority order in an annex of the CISP.
���������� C14.1.4.� The CISP will define specific CI support to
be provided to each RDT&E facility and acquisition program and will provide
the servicing CI personnel with information about the facility or program being
supported.
C14.2.� CI ACTIONS AT RDT&E ACTIVITIES
���������� C14.2.1.� Component CI agencies have identified a core
listing of CI services that are recommended for each CISP.
���������� C14.2.2.� If there is CRT at a RDT&E site, the
site director-approved CISP will be provided to the Service CI specialists
working at the RDT&E site.�
���������� C14.2.3.� If there is CPI at a RDT&E site, the
PM-approved CISP will be provided to the Service CI specialists working at the
site and will become an annex to the site CISP.
���������� C14.2.4.� If CPI or CRT is identified at a DoD
contractor facility, the PM CI specialist, the DSS CI specialist, and the
contractor will develop a CISP annex (CISP-A) to define the CI support to the
contractor.� (The DSS-format for a
contractor CISP-A is in the Specialized C3I Operating Reference (SCOR).)
���������� C14.2.5.� If RDT&E site management identifies CRT
or CPI requiring specialized CI support beyond what is covered in the project
or program CISP, that additional support will be documented as an annex to the
site CISP.
���������� C14.2.6.� Component CI personnel supporting CRT or CPI
will keep the Project or PM�s CI POC informed of threat and other information
adversely impacting the CRT or CPI.� The
CI POC is responsible for keeping the PM or site director apprised of current
CI activities.
���������� C14.2.7.� When more than one Component CI agency has
an interest at the same RDT&E site or contractor facility, teaming and
cooperation should occur at the lowest possible level.� If conflict occurs and is irresolvable at
the Component level, information on the conflict may be sent to the Director,
Counterintelligence, OASD(C3I), for review and resolution.
C14.3.� CI SUPPORT PLAN
���������� C14.3.1.� The CISP will be signed by local CI and site
management personnel, the PM, or local DSS representative, as appropriate.� The CISP will be reviewed and updated
annually, or immediately based upon events.�
A copy of the signed plan will be provided to the Service CI
headquarters.
���������� C14.3.2.� Any updated CISP should be redistributed to
those providing support.
���������� C14.3.3.� A recommended format for the CISP is in the
SCOR.� Component CI headquarters may
modify this format.
C15. CHAPTER 15
ANTI-TAMPER TECHNIQUES
C15.1� GENERAL
�������� C15.1.1.� Anti-Tamper (AT) encompasses those systems engineering activities intended to prevent and/or delay exploitation of critical technologies in U.S. defense systems.� These activities involve the entire life cycle of systems acquisition and include research, design, development, implementation, and testing of AT measures.
����������
���������� C15.1.2.� AT will be initiated in the program definition and risk reduction phase in conjunction with the identification of the program CRT and/or CPI.� AT is applicable to Pre-Planned Product Improvement (P3I) upgrades or other technology insertion to fielded systems.
���������� C15.1.3.� AT requires resources, and thus may affect other aspects of the program, to include cost and performance of the end item.� AT involves risk analysis.� The decision not to implement AT must be based on operational risks involved, as well as on acquisition risks including, but not limited to, feasibility, cost, system performance impacts, and schedule impacts.
���������� C15.1.4.� The DoD Executive Agent for AT resides with the Department of the Air Force.� The Executive Agent will be responsible for implementing AT policy and associated technology development.� The Executive Agent coordinates technology development, is responsible for developing the AT technology roadmap, and creating a shared common databank/library.� DoD Components will continue the development of AT technology, maintain AT focal points, and implement AT into their respective programs.� It is important that each DoD Component maintain a core of AT knowledgeable individuals to assist the PM with the insertion of AT technology into their respective programs.� The PM may seek advice, assistance, and access to other organizations that have AT capabilities by contacting their Component AT POC and the DoD AT Executive Agent (SAF/AQL).
���������� C15.1.5.� Systems engineering activities intended to prevent and/or delay exploitation of CRT and/or CPI in U.S. defense systems may also include system security engineering (SSE) activities (see C12.� Chapter 12).
C15.2.� APPLICATION OF AT
�������� C15.2.1.� The PM is responsible for determining whether AT applies to a system or multiple systems being acquired.� This determination will be based on the sensitivity of the technologies to be used.� It is feasible the evaluation may indicate there is no requirement to apply AT techniques to the technologies being used or planned.� AT should not be regarded as an option or capability to be used in a trade-off without thorough operational and acquisition risk analyses.�
�������� C15.2.2.� AT applies to all acquisition categories of DoD programs using critical research technologies, whether the program is in development, undergoing P3I, or other technology insertion efforts.�
���������� C15.2.3.� AT shall be considered for use on any system co-developed with allied partners, likely to be sold or provided to U.S. allies or friendly foreign governments, or likely to fall under adversarial control.� If the system is not likely to be exposed to these scenarios, then AT may not be required.� The PM assessment and subsequent MDA decision, however, must be deliberate, fully supported, and documented in the PPP.
�������� C15.2.4.� U.S. defense systems not intended for foreign distribution through foreign military sales, direct commercial sales, or other avenues but that may fall under adversarial control during combat, hostile action, or other scenarios will include AT if critical technologies are involved and documented in the PPP.
�������� C15.2.5.� The PM will coordinate with appropriate comptroller and financial management organizations to obtain program funding for AT.� The PM will ensure that funding or changes to funding are not made without proper justification based on risk analysis.
�������� C15.2.6.� AT will be included in requirements development for all new acquisition programs.� AT will not be required for fielded systems or those that have passed Milestone B, since AT may be difficult or impractical to retrofit.� However, AT will be considered in any product improvement engineering effort or engineering change proposals for these systems.� AT may be required, regardless of the acquisition program status, at the discretion of the MDA.
�������� C15.2.7.� AT applicability will be assessed for each major modification or P3I upgrade to the production system.� It is feasible that AT may be inserted into the modified or upgraded systems when protection is required.� AT may be discontinued when it is determined the technology no longer needs protection.
�������� C15.2.8.� The PM recommendation whether or not to implement AT will be approved by the MDA.� This decision will be documented in the PPP.
C15.3.� AT IMPLEMENTATION
���������� C15.3.1.� The need for AT will be identified in the PPP.� An AT annex will be classified as appropriate and updated with each PPP revision.�
�������������� C15.3.1.1.� The AT classified annex to the PPP will contain AT planning.� The planning detail will correspond to the acquisition phase of the program.�
�������������� C15.3.1.2.� The AT annex should include, but is not limited to, the following information:�
����������������� C15.3.1.2.1.� Identification of the critical technology being protected and its criticality to the system�s performance.
����������������� C15.3.1.2.2.� Determination of how long AT is intended to delay hostile or foreign exploitation or reverse-engineering efforts.
����������������� C15.3.1.2.3.� Description of the planned AT approach.
����������������� C15.3.1.2.4.� The effect that compromise would have on the acquisition program if AT is not implemented.
����������������� C15.3.1.2.5.� The estimated time and cost required for system or component redesign if compromise occurs.
����������������� C15.3.1.2.6.� The PM recommendation and the MDA decision on AT.
����������������� C15.3.1.2.7.� The program AT POC.
�������������� C15.3.1.3.� The AT annex to the PPP will be developed for Milestone B and be updated at subsequent milestones.
�������������� C15.3.1.4.� AT costs will be included in security cost estimates by an individual line item within the Planning, Programming, and Budgeting System.
���������� C15.3.2.� AT will be reflected in system specifications, integrated logistics support plan, and other program documentations.
���������� C15.3.3.� AT, whether implemented or not, will be a discussion item at Milestone B, Milestone C (Low-Rate Initial Production), and Full-Rate Production Decision Reviews.�
�������������� C15.3.3.1.� At Milestone B, AT should be addressed in conceptual terms of how it is to be implemented.� Working AT prototypes, appropriate to this stage of program development, should be demonstrated.� Deliverables at Milestone B will include:� a list of critical technologies, a MDCI threat analysis, a list of identified vulnerabilities, and a preliminary AT requirement.� These deliverables will be submitted and incorporated into the AT Annex of the PPP.
�������������� C15.3.3.2.� The Milestone C decision should not be given favorable consideration until AT implementation is fully documented and tested during developmental test and evaluation (DT&E) and operational test and evaluation (OT&E), and ready for production.� Deliverables at Milestone C will include:� all deliverables from Milestone B and any updates; an analysis of AT methods that apply to the system, including cost/benefit assessments; an explanation of which AT methods will be implemented; and a plan for validating the AT implementation.� These deliverables will be submitted and incorporated into the AT annex of the PPP.
C15.4.� AT VERIFICATION AND VALIDATION
�������� C15.4.1.� The AT implementation will be tested and verified during the program DT&E and OT&E.�
�������� C15.4.2.� The PM will develop the validation plan and provide the necessary funding and actual or representative system components.� The PM validation plan, developed in Milestones B and C, will be reviewed by the AT Executive Agent prior to each milestone decision.� The AT Executive Agent will perform the validation after system deployment.�
�������� C15.4.3.� The validation results shall be reported to the appropriate Service Acquisition Executive and OUSD(AT&L).
C15.5.� SUSTAINMENT OF AT
�������� C15.5.1.� AT is not limited to development and fielding of a system.� It is equally important during life cycle management of the system, particularly during maintenance.�
�������� C15.5.2.� Maintenance instructions, technical orders, and training documents must clearly indicate that AT techniques have been implemented, the level at which maintenance is authorized, and warnings that damage may occur if improper or unauthorized maintenance is attempted.�
�������� C15.5.3.� It may be necessary to limit the level and extent of maintenance that a foreign customer may perform in order to protect critical technologies.� This may mean that the level of maintenance that involves AT will be accomplished only at U.S. contractor or U.S. Government facilities.� Such maintenance restrictions may be no different than those imposed on U.S. Government users of AT protected systems.�
�������� C15.5.4.� Maintenance and logistics restrictions must be stated in the appropriate contracts, project arrangements, memoranda of agreement, memoranda of understanding, letters of offer and acceptance, or other similar documents.�
�������� C15.5.5.� The U.S. Government and U.S. industry must be protected against warranty and performance claims in the event AT measures are activated by unauthorized maintenance or other intrusion.� Such unauthorized activities shall be regarded as hostile attempts to exploit or reverse engineer the system or the AT measures and shall void warranties and performance guarantees.
C15.6.� GUIDELINES FOR AT DISCLOSURE
�������� C15.6.1.� The fact that AT has been implemented in a program should be unclassified unless the appropriate disclosure authority of the DoD Component, in consultation with the program PEO, SAE, or MDA, has decided that the fact should be classified.�
�������� C15.6.2.� The measures used to implement AT may be classified at any level including any special handling caveats or access requirements.� Classified AT information, including information concerning AT techniques, will not be disclosed to any unauthorized individual or non-U.S. interest pursuant to decisions made by appropriate disclosure authorities.�
�������� C15.6.3.� Such disclosure decisions will take into account the guidance and recommendations of the program PEO, SAE, or MDA and those of USD(P).� The program PEO, SAE, or MDA shall coordinate all foreign disclosure releases involving AT with the cognizant foreign disclosure authority and security assistance office, as appropriate.� An exception to National Disclosure Policy may be warranted for co-development programs, foreign military sales, or direct commercial sales.
C15.7.� REVIEW OF AT
�������� C15.7.1.� The Director of Strategic and Tactical Systems, OUSD(AT&L)/S&TS will convene a standing OIPT to guide the use of AT, and to review issues, decisions, and progress of the DoD overall AT initiative.
�������� C15.7.2.� SAEs, USD(P), and OUSD(AT&L)/S&TS will be kept apprised of the AT status in any program, including P3I to fielded systems, as well as AT employed in a SAP.
�������� C15.7.3.� The MDA will review and approve AT recommendations and implementation plans that will be documented in an AT annex to the PPP.�
C16. CHAPTER 16
HORIZONTAL ASSESSMENT AND PROTECTION
C16.1.� GENERAL
������� C16.1.1.� The objective of horizontal assessment and protection activities is to ensure consistent, cost-effective application of similar RTP safeguards for similar CRT and/or CPI throughout DoD.�
������� C16.1.2.� Conducting horizontal assessment determines whether similar technologies are being used in different programs.�
������� C16.1.3.� Horizontal protection responds to these assessments by ensuring that similar technologies are being safeguarded with the same level of protection.
������� C16.1.4.� The ASD(C3I), the USD(AT&L), and the DOT&E provide oversight of the effectiveness of horizontal assessment and protection as outlined in DoD Directive 5200.39 (reference (a)).
C16.2.� HORIZONTAL ASSESSMENTS
������� C16.2.1.� Horizontal assessments should address the following:
���������������� C16.2.1.1.� System enabling technologies (CRT and/or CPI) and their additional applications, whether for similar or dissimilar tasks.
���������������� C16.2.1.2.� RTP safeguards planned or provided.
���������������� C16.2.1.3.� Intelligence estimates of competitive foreign acquisition efforts.
���������������� C16.2.1.4.� Reports of completed investigations of compromises, espionage cases, and other losses.
������� C16.2.2.� DoD Components should establish processes needed to support horizontal assessment and protection activities.� The DoD Components should do the following:
���������������� C16.2.2.1.� Identify system enabling technologies and their additional applications, whether for similar or dissimilar tasks.
���������������� C16.2.2.2.� Review security classification guides of existing programs or projects when developing a CISP, SSP, or PPP to determine classification of similar technologies used in other programs or under development.� See DoD O-5200.1-I (reference (rr)).
���������������� C16.2.2.3.� Catalogue, analyze, group, and correlate protection requirements within approved PPPs for CPI or SSPs for CRT involving similar enabling technologies.� Provide the data collected to the JCAG for their use.
������� C16.2.3.� JCAG is responsible for conducting horizontal assessments throughout DoD to ensure that similar safeguards are applied to similar technologies.�
C16.3.� HORIZONTAL PROTECTION
������� C16.3.1.� JCAG will provide its assessment report to the site director for emerging technologies and/or to the PM for their application within an acquisition program.�
������� C16.3.2.� Site directors or PMs should ensure their respective SSP, CISP, and PPP are modified when required based upon results of the horizontal assessments.
������� C16.3.3.� JCAG will coordinate all reported or discovered discrepancies with the DoD Components for resolution at the lowest level possible.�
������� C16.3.4.� JCAG will report unresolved inconsistent applications of RTP safeguards, when necessary, to the USD (AT&L), DOT&E, and ASD (C3I) for resolution by the DRTPC within 30 days.� Copies of these reports will be provided to the DoD Inspector General (IG).
C16.4.� REPORTING REQUIREMENTS
������� Compromise of CRT or CPI will be reported to the DRTPC and through CI channels to JCAG and the ASD(C3I), in accordance with DoD Instruction 5240.4 (reference aa)).
C17.� CHAPTER 17
RTP ASSESSMENT AND INSPECTION
C17.1.� GENERAL
���������� Periodic assessments and inspections of RTP activities (encompassing all DoD RDT&E budget categories) are necessary to ensure effective RTP is being planned and implemented.� The DoD Component responsible for the RDT&E site or the acquisition program is responsible for these assessments and inspections (DoD Directive 5200.39 (reference (a)).
C17.2.� ASSESSMENTS
���������� DoD Components will periodically assess and evaluate the effectiveness of RTP in the implementation by RDT&E site directors and PMs as well as the support provided by security, intelligence, and CI to RDT&E sites and acquisition programs with CRT or CPI.
C17.3.� INSPECTIONS
���������� C17.3.1.� The DoD Inspector General (IG) will ensure a uniform system of periodic inspections, through existing agency and service inspection processes, for RDT&E site compliance with directives concerning security, RTP, and CI practices.�
���������� C17.3.2.� The DoD IG will develop RTP inspection guidelines for use by DoD and DoD Component Inspectors General.� These guidelines will enhance consistent application of directives that apply to RTP directives and related issuances.
���������� C17.3.3.� Inspection guidelines are in the Specialized C3I Operating Reference (SCOR).
���������� C17.3.4.� DoD Component IGs will conduct inspections using the DoD IG inspection guidelines.� These inspections will include periodic inspections of acquisition programs and RDT&E sites for compliance with appropriate RTP directives.
���������� C17.3.5.� Ensure that DoD Component IG inspections assess site director and PM compliance with Section C11.3. above, Assessment of PPP Effectiveness,.
���������� C17.3.6.� Copies of DoD Component IG inspection reports will be provided to the USD(AT&L) and the ASD(C3I).
���������� C17.3.7.� The DoD IG will conduct periodic audits of DoD Component IG inspections for compliance with RTP directives and related issuances.
C18.� CHAPTER
18
INFORMATION ASSURANCE
C18.1.� GENERAL
C18.1.1.� In today�s environment of sophisticated
weaponry and rapid global force projection requirements, the ability to provide
timely and accurate information is vital to all aspects of DoD operations.�
C18.1.2.� Information Assurance (IA) is a critical
component of DoD operational readiness, providing the means to detect, react,
and restore vital information services as efficiently and effectively as
possible.� IA contributes to DoD�s
requirement to transition from peacetime through exigent operations in conflict
and back to peacetime in the execution of its mission to defend U.S. interests.� This depends on maintaining an interconnected
set of information systems and networks referred to as the Global Information
Grid (GIG).�
C18.1.3.� Office of Management and Budget (OMB)
Circular A-130 (reference (ss)) mandates DoD to implement and maintain a
program to ensure adequate security is provided for all agency information
systems or major applications, as follows:
����������������� C18.1.3.1.� Assign responsibility for security.
����������������� C18.1.3.2.� Develop a security plan that defines:� rules of behavior concerning use of,
security in, and the acceptable level of risk for the system; training for all
appropriate users and administrators; personnel controls; incident response
capability; continuity of support; technical security; and system
interconnection.
����������������� C18.1.3.3.� Review security controls at least every
three years.
����������������� C18.1.3.4.� Management authorization of systems to
process information.
C18.1.4.� It is within these broad Federal guidelines
the DoD is directed how IT systems within the Department will be acquired,
operated, and protected through comprehensive IA strategies and practices.� The foundation documents are as follows:
����������������� C18.1.4.1.� Defense Acquisition policies:� DoD Directive 5000.1 (reference (n)), DoD
Instruction 5000.2 (reference (b)), and DoD 5000.2-R (reference (o)).
����������������� C18.1.4.2.� DoD Global Information Grid Information
Assurance Policy Memorandum No. 6-8510 (reference (tt)).
����������������� C18.1.4.3.� DoD Information Technology Security
Certification and Accreditation Process (DITSCAP):� DoD Instruction 5200.40 (reference (uu)) and DoD 8510.1-M
(reference (vv)).
C18.1.5.� Global Information Grid Information
Assurance Policy Memorandum 6-8510 (reference (tt)) and DoD Instruction 5200.40
(reference (uu)) establish details for developing an IA strategy for any
appropriate program, from concept exploration through fielding of a system, and
then periodic re-accreditation.� This
planning includes the incorporation of security requirements into the system
requirement documents, design, and operation.�
Costs associated with IA should be considered during analysis of
alternatives, life-cycle cost estimating, test planning, and developing the
acquisition program baseline.
C18.1.6.� IA plans
C18.2.� SYSTEM SECURITY AUTHORIZATION AGREEMENT
���������� C18.2.1.� The DITSCAP process provides a sound IA
strategy in the System Security Authorization Agreement (SSAA).� Applicable SSAAs with be annexes to the
PPP.� Associated costs will be recorded
in the PPP by fiscal year.
���������� C18.2.2.� The DITSCAP establishes a standard process,
set of activities, general task descriptions, and a management structure to
certify and accredit IT systems throughout the system life cycle.� The SSAA documents an agreement between the
PM or project manager, the Designated Approval Authority (DAA), the
Certification Authority (CA), and the user representative concerning schedule,
budget, security, functionality, risk, and performance issues.
���������� C18.2.3.� The SSAA is a living document describing the
security planning status of the program at any given point in the acquisition
cycle.� All levels of management
responsible to the DoD Component Chief Information Officer (CIO) for oversight
of the program should review the SSAA.�
DoD Components should enlist the services of security professionals or
organizations in building sound IA practices into every program and documenting
this strategy within the SSAA.
���������� C18.2.4.� The SSAA confirms that a program has an IA
strategy consistent with DoD policies and architecture.� The DoD Component CIO reviews the SSAA.� The DoD CIO certifies the SSAA to indicate
the program has sufficient IA strategy as required before milestone approval or
certification in accordance with the Clinger-Cohen Act of 1996 (reference
(ww)).�
AP1.� APPENDIX 1
EXPORT CONTROL DECISION GUIDE
This Guide is intended to assist laboratory scientists,
engineers, and cooperative program personnel in determining if their programs
or projects involve Export Controlled Technical Data.� �
This Guide does not authorize any release
and is for informational purposes only.
�
Only a Designated Disclosure Authority or higher authority
may authorize any release to foreign entities or individuals. Public Affairs
Office after security review will approve all public releases.
AP1.1.� This guide is designed to be helpful in defining and distinguishing the difference between Export Controlled and Public Domain information.� Sometimes people use the terms Technical Data, Public Domain, Basic Research, Fundamental Research, University Research, and / or other variants interchangeably.� This guide will provide the resources to help clarify these differences.
AP1.2.� The International Traffic in Arms Regulation (ITAR) establishes a significant definition on what is not Public Domain.� ITAR Part 120.11 states, �Fundamental research is defined to mean:� basic and applied research in science and engineering, where the resulting information is ordinarily published and shared broadly within the scientific community.�� This provides a distinction from research the results of which are restricted for proprietary reasons or specific U.S. Government access and dissemination controls.
AP1.3.� The following links are two primary sources to determine if the technology (e.g., software, data, information, end item, manufacturing process) is export controlled:�
Department of Commerce Export Control List� http://www.access.gpo.gov/bxa
Department of State's United States Munitions List� http://www.pmdtc.org/USML.pdf.
AP1.4.� U.S. persons and entities are responsible for compliance with the International Traffic in Arms Regulations (ITAR) governing export of Defense items, services, and technologies.� The ITAR is issued by the U. S. State Department.� U.S. persons and entities are also responsible for compliance with the Export Administration Regulation (EAR) which governs the export of Dual-Use items, services and technologies.� The Export Administration Regulation (EAR) is issued by the U.S. Department of Commerce/BXA.� Information on U.S. dual-use export controls can be found on the Bureau of Export Administration Exporter Assistance web page (http://www.bxa.doc.gov/factsheets/ExporterAssistance.html).
AP1.4.1.� Information on all other U.S. Government export controls, and the agencies that hold various export control responsibilities, can be found at:
Bureau of Export Administration Resource Links web page (http://www.bxa.doc.gov/reslinks.htm).
AP1.4.2.� Additionally, exports from the United States may be subject to other regulations, including those administered by:
Department of Energy (nuclear technology) (http://www.energy.gov/security/)
Nuclear Regulatory Commission (nuclear equipment and materials) (http://www.nrc.gov/NRC/nucmat.html)
Department of the Treasury (embargoes) (http://www.ustreas.gov/)
AP1.5.� For Clarification:� Any disclosure or release (Export) to a foreign national in the U.S. or export out of the United States requires there to be an authorized approval before release.� This approval can be a Commercial Export License, Foreign Military Sale, or an established government-to-government agreement.� This approval document needs to exist between the U.S. person or entity and the foreign country involved for that specific technology, information, and/or end item, which is the subject of the proposed transfer.
AP1.5.1.� Export.� The legal definition of �Export� is:
�������� AP1.5.1.1.� Sending or taking a defense article out of the United States in any manner, except by mere travel outside of the United States by a person whose personal knowledge includes technical data.
�������� AP1.5.1.2.� Transferring registration, control or ownership to a foreign person of any aircraft, vessel, or satellite covered by the U.S. Munitions List, whether in the United States or abroad.
�������� AP1.5.1.3.� Disclosing (including oral or visual disclosure) or transferring in the United States any defense article to an embassy, any agency or subdivision of a foreign government (e.g., diplomatic missions).
�������� AP1.5.1.4.� Disclosing (including oral or visual disclosure) or transferring technical data to a foreign person, whether in the United States or abroad.
�������� AP1.5.1.5.� Performing a defense service on behalf of, or for the benefit of, a foreign person, whether in the United States or abroad.
AP1.5.2.� Temporary Import:� The legal definition of �temporary import� is:
�������� AP1.5.2.1.� Bringing into the United States from a foreign country any defense article that is to be returned to the country from which it was shipped or taken or any defense article that is in transit to another foreign destination.
�������� AP1.5.2.2.� Temporary import includes withdrawal of a
defense article from a customs bonded warehouse or foreign trade zone for the
purpose of returning it to the country of origin or country from which it was
shipped or for shipment to another foreign destination.� The Department of the Treasury regulates
permanent imports (see 27 CFR parts 47, 178, and 179).
���������� AP1.5.3.� Release to Foreign Nationals:� If a foreign national is provided knowledge or insight, or has �hands on� contact with these controlled items without the appropriate DoD Component, DoD, Department of State, or Department of Commerce approval, a Federal Statute may have been violated.
���������� AP1.5.4.� Exceptions and Exemptions:� There are certain exceptions or exemptions that may be applicable.� Inquiries to determine whether they apply should be directed through your local Foreign Disclosure Office to the primary Foreign Disclosure and/or Technology Transfer office on a case-by-case basis.
���������� AP1.5.5.� Determining if an Agreement already exists:� To determine the existence of an international agreement between the U.S. and a foreign country involving a specific technology and or international cooperative agreement, contact the applicable DoD or Military Department armaments cooperative division.
����������������������� AP1.5.5.1.� If there is an established international agreement, consult your local Foreign Disclosure Officer to determine what is and/or is not releasable under the terms of the Delegation of Disclosure Authority Letter (DDL).
����������������������� AP1.5.5.2.� Do not use the Militarily Critical Technologies List (MCTL), sometimes referred to as the Military Critical Technologies (MCT), as a basis to determine if an item is export controlled.� This document does not list export-controlled items.
AP1.6.� Public Affairs Requirements:� The DoD has a specific requirement for a security review prior to public release of information.� This review may be performed by the public affairs and security offices.� The public affairs office provides a review guide that is an excellent tool to assist in determining if the research project involves anything other than public domain information.
AP1.7.� Proprietary Information:� If proprietary information is involved, a written release will be requested from the owner of the proprietary information.� The written release must specify foreign person and country to which the proprietary information will be given.
Attachments:
AP1.A1.� Department of Commerce Export Control Guidance
AP1.A2.� Department of State Export Control Guidance
AP1.A3.� Frequently Asked Questions on Commerce Control Issues
AP1.A1.� ATTACHMENT 1 TO APPENDIX
1
DEPARTMENT OF
COMMERCE
EXPORT CONTROL GUIDANCE (OVERVIEW)
AP1.A1.1.� What is Commerce Department controlled
�technology�?
Per Part 772 of the Export Administration Regulations (EAR), �technology� is specific information necessary for the �development,� �production,� or �use� of a product.
The General Technology Note states that the �export of technology � is controlled according to the provisions of each Category.�� It further states that �technology required for the development, production, or use of a controlled product remains controlled even when applicable to a product controlled at a lower level.�
Please note that the terms:� �required,� �development,� �production,� �use,� and �technologies� are all defined in Part 772 of the EAR.
Controlled technology is that which is listed on the Commerce
Control List.
AP1.A1.2.� Technology is considered released, exported, and / or disclosed when:� Technology is �released� for export when it is available to foreign nationals for visual inspection (such as reading technical specifications, plans, blueprints, etc.); when technology is exchanged orally; or, when technology is made available by practice or application under the guidance of persons with knowledge of the technology.� See �734.2(b)(3) of the Export Administration Regulations (EAR).
���������� AP1.A1.2.1.� Definitions of export (Para 734.2):
�������������������� AP1.A1.2.1.1. ��Export� means an actual shipment or transmission of items subject to the EAR out of the United States, or release of technology or software subject to the EAR to a foreign national in the United States, as described in paragraph (b)(2)(ii) of this section.� See paragraph (b)(9) of this section for the definition that applies to exports of encryption source code and object code software subject to the EAR.
�������������������� AP1.A1.2.1.2.� Export of technology or software.� (See paragraph (b)(9) for provisions that apply to encryption source code and object code software.) �Export� of technology or software, excluding encryption software subject to �EI� controls, includes:� Any release of technology or software subject to the EAR in a foreign country; or, Any release of technology or source code subject to the EAR to a foreign national.� Such release is deemed to be an export to the home country or countries of the foreign national.� This deemed export rule does not apply to persons lawfully admitted for permanent residence in the United States and does not apply to persons who are protected individuals under the Immigration and Naturalization Act (8 U.S.C. 1324b(a)(3)).� (Note that the release of any item to any party with knowledge a violation is about to occur is prohibited by �736.2(b)(10) of the EAR.)
AP1.A1.3.� What technologies are subject to the
Commerce Department controls ?
���������� AP1.A1.3.1.� Generally, technologies subject to the Export Administration Regulations (EAR) are those which are in the United States or of U.S. origin, in whole or in part.� Most are proprietary.� Technologies which tend to require licensing for transfer to foreign nationals are also dual-use (i.e., have both civil and military applications) and are subject to one or more control regimes, such as National Security, Nuclear Proliferation, Missile Technology, or Chemical and Biological Warfare.
���������� AP1.A1.3.2.� Technologies, which may require an export license, are those which are subject to the EAR and which are listed in the Commerce Control List (see Parts 734, 738, and 774 of the EAR).
���������� AP1.A1.3.3.� Foreign technology with U.S.-origin technology commingled to a degree above a de minimis level is considered to be subject to the EAR.
���������� AP1.A1.3.4.� Some technologies are under the exclusive jurisdiction of another agency of the U.S. Government and are not subject to the EAR.� These include defense services, which are under the jurisdiction of the State Department, and technology related to the production of special nuclear materials, which is under the jurisdiction of the Energy Department.
AP1.A1.4.� Federal Contract Controls:� In a contract for performance of research entered into with the Department of Defense (DoD), certain national security controls are agreed upon.� DoD is to have ninety days to review any papers proposed before they are published and must approve assignment of any foreign nationals to the project.� The work in question would otherwise, if not identified as being controlled, qualify as �fundamental research�.� See section �734.8 of the EAR.� The following provides a more comprehensive analysis:
���������� AP1.A1.4.1.� Under �734.11 of the EAR, any export or re-export of information resulting from government-sponsored research that is inconsistent with contract controls you have agreed to will not qualify as �fundamental research� and any such export or re-export would be subject to the EAR.
���������� AP1.A1.4.2.� Any such export or re-export that is consistent with the controls will continue to be eligible for export and re-export under the �fundamental research� rule set forth in �734.8(a) of the EAR.� Thus, if you abide by the specific controls you have agreed to, you need not be concerned about violating the EAR.
���������� AP1.A1.4.3.� If you violate these controls and export or re-export information as �fundamental research� under �734.8(a) of the EAR, you may subject yourself to the sanctions provided for under the EAR, including criminal sanctions, in addition to administrative and civil penalties for breach of contract under other laws.
AP1.A1.5.� Is Software is considered �technology� and
is it similarly controlled?
���������� The Export Administration Regulations (EAR) definitions distinguish between software and technology.� Software is one of the groups within each of the categories of items listed on the Commerce Control List (CCL). Software, which is delineated on the CCL, is controlled.
AP1.A1.6.� What is the �deemed export� rule?
���������� An export of technology or source code (except encryption source code) is �deemed� to take place when it is released to a foreign national within the United States.� See �734.2(b)(2)(ii) of the Export Administration Regulations (EAR).
AP1.A1.7.� Technologies considered �fundamental
research� by the Department of Commerce:
���������� AP1.A1.7.1.� �Fundamental research� is basic and applied research in science and engineering where the resulting information is ordinarily published and shared broadly within the scientific community.
�
���������� AP1.A1.7.2.� It is distinguished from proprietary research and from industrial development, design, production, and product utilizations, the results of which ordinarily are restricted for proprietary and/or specific national security reasons.
���������� AP1.A1.7.3.� Normally, the results of �fundamental research� are published in scientific literature, thus making it publicly available.� Research which is intended for publication, whether it is ever accepted by scientific journals or not, is considered to be �fundamental research.�� A large segment of academic research is considered �fundamental research.�
���������� AP1.A1.7.4.� Because any information, technological or otherwise, that is publicly available is not subject to the Export Administration Regulations (EAR), (except for encryption object code and source code in electronic form or media) and thus does not require a license, �fundamental research� is not subject to the EAR and does not require a license.� Please see �734.8 of the EAR for a full discussion.
AP1.A1.8.� What is University-based research?
���������� AP1.A1.8.1.� Research conducted by scientists, engineers, or students at a university normally will be considered fundamental research, as described in paragraphs 734.8 (b)(2) through (6) of this section.� (�University� means any accredited institution of higher education located in the United States.)
���������� AP1.A1.8.2.� Prepublication review by a sponsor of university research solely to insure that the publication would not inadvertently divulge proprietary information that the sponsor has furnished to the researchers does not change the status of the research as fundamental research.� However, release of information from a corporate sponsor to university researchers where the research results are subject to prepublication review, is subject to the EAR.
���������� AP1.A1.8.3.� Prepublication review by a sponsor of university research solely to ensure that publication would not compromise patent rights does not change the status of fundamental research
���������� AP1.A1.8.4.� The initial transfer of information from an industry sponsor to university researchers is subject to the EAR where the parties have agreed that the sponsor may withhold from publication some or all of the information so provided.
���������� AP1.A1.8.5.� University-based research is not considered �fundamental research� if the university or its researchers accept (at the request, for example, of an industrial sponsor) other restrictions on publication of scientific and technical information resulting from the project or activity.� Scientific and technical information resulting from the research will nonetheless qualify as fundamental research once all such restrictions have expired or have been removed.
���������� AP1.A1.8.6.� The provisions of �734.11 of the EAR will apply if a university or its researchers accept specific national security controls (as defined in �734.11 of this part) on a research project or activity sponsored by the U.S. Government.
AP1.A1.9.� Research based at Federal agencies or
FFRDCs:
Research conducted by scientists or engineers working for a
Federal agency or a Federally Funded Research and Development Center (FFRDC)
may be designated as �fundamental research� within any appropriate system
devised by the agency or the FFRDC to control the release of information by
such scientists and engineers.� (Note:
Technology which has been identified to be controlled is not �fundamental research�.)
AP1.A1.10.� Corporate research: �Research conducted by scientists or engineers working for a business entity will be considered �fundamental research� at such time and to the extent that the researchers are free to make scientific and technical information resulting from the research publicly available without restriction or delay based on proprietary concerns or specific national security controls as defined in �734.11(b) of the EAR.
���������� AP1.A1.10.1.� Prepublication review by the company solely to ensure that the publication would compromise no proprietary information provided by the company to the researchers is not considered to be a proprietary restriction.
���������� AP1.A1.10.2.� Prepublication review by the company solely to ensure that publication would compromise no patent rights will not be considered a proprietary restriction for this purpose, so long as the review causes no more than a temporary delay in publication of the research results.
���������� AP1.A1.10.3.� However, the initial transfer of information from a business entity to researchers is not authorized under the �fundamental research� provision where the parties have agreed that the business entity may withhold from publication some or all of the information so provided.
AP1.A1.11.� Educational Information:� �Educational information� referred to in �734.3(b)(3)(iii) is not subject to the EAR if it is released by instruction in catalog courses and associated teaching laboratories of academic institutions.� A distinct review must be made and approved before it is provided in a manner, which would result in public release.� Dissertation research is discussed in �734.8(b) of this part.� Note that the provisions of this section do not apply to encryption software controlled under ECCN 5D002 for �EI� reasons on the Commerce Control List (refer to ��740.13 (e) and 740.17(a)(5)(i) of the EAR for release under License Exception)
AP1.A1.12.� Is a foreign national subject to the �deemed
export� rule?
���������� AP1.A1.12.1.� Any foreign national is subject to the �deemed export� rule. This includes all persons in the U.S. as tourists, students, businesspeople, scholars, researchers, technical experts, sailors, airline personnel, salespeople, military personnel, diplomats, etc.
���������� AP1.A1.12.2.� Exceptions do exist for a foreign national who:
���� AP1.A1.12.2.1.� Is granted permanent residence, as demonstrated by the issuance of a permanent resident visa (i.e., �Green Card�); or
���� AP1.A1.12.2.2.� Is granted U.S. citizenship; or
���� AP1.A1.12.2.3.� Is granted status as a �protected person� under 8 U.S.C. 1324b(a)(3). As noted, one exception to this general statement is a �protected person.�� �Protected persons� include political refugees and political asylum holders.� Be aware that individuals seeking �protected person� status must satisfy all of the terms and conditions that are fully set forth in 8 U.S.C. 1324b(a)(3
AP1.A1.13. �Permanent
residents or citizens of countries other than those of their nationality
���������� AP1.A1.13.1.� If the individual is a naturalized citizen or permanent resident of the United States, the �deemed export� rule does not apply.� In other words, he or she is not subject to the provisions of the �deemed export� regulation.
���������� AP1.A1.13.2.� For individuals who are citizens of more than one foreign country, or have citizenship in one foreign country and permanent residence in another, as a general policy, the last permanent resident status or citizenship obtained governs.� If, for some reason, the status of a foreign national is not certain, then you should ask the Bureau of Export Administration (BXA), to determine where the stronger ties lie, based on the facts of the specific case.
���������� AP1.A1.13.3.� The status of a foreign national could be critical in situations where information may indicate involvement with prohibited entities or activities (for example, missile or nuclear-related end-uses or end-users as identified in Part 744 of the EAR)
���������� AP1.A1.13.4.� In response to a request for the status of a foreign national, BXA will look at the foreign national's family, professional, financial, and employment ties.
AP1.A2.� ATTACHMENT 2 TO APPENDIX
1
DEPARTMENT OF STATE
POINT PAPER ON EXPORT CONTROL GUIDANCE
AP1.A2.1.� Background:
���������� Section 38
of the Arms Export Control Act (22 U.S.C. 2778) authorizes the President to
control the export and import of defense articles and defense services.� The statutory authority of the President to
promulgate regulations with respect to exports of defense articles and defense
services was delegated to the Secretary of State by Executive Order 11958, as
amended (42 FR 4311).� This subchapter
implements that authority.� By virtue of
delegations of authority by the Secretary of State, the Director of the Office
of Defense Trade Controls, Bureau of Politico-Military Affairs, Department of
State primarily administers these regulations.�
���������� Only U.S. persons (as defined in the ITAR �120.15) and foreign governmental entities in the United States may be granted licenses or other approvals (other than retransfer approvals sought pursuant to this subchapter).� Foreign persons (ITAR 120.16) other than governments are not eligible.
���������� Applications
for licenses or other approvals will be considered only if the applicant has
registered with the Office of Defense Trade Controls.� All applications and requests for approval must be signed by a
U.S. person who has been empowered by the registrant to sign such documents.
AP1.A2.2.�
Designation of defense articles and defense services.� The Arms Export Control Act (22 U.S.C.
2778(a) and 2794(7)) provides that the President shall designate the articles
and services deemed to be defense articles and defense services for purposes of
this subchapter.� The items so
designated constitute the United States Munitions List.� The Department of State makes such
designations with the concurrence of the Department of Defense.� For a determination on whether a particular
item is included on the U.S. Munitions List see ITAR �120.4(a).
AP1.A2.3.� Policy on designating and
determining defense articles and services.
�
An article or service may be designated or determined in the future to be a
defense article� (see ITAR 120.6) or
defense service (ITAR �120.9) if it:
���������� AP1.A2.3.1.� Is specifically designed, developed, configured, adapted, or modified for a military application, and
���������� AP1.A2.3.2.� Does not have predominant civil applications, and
���������� AP1.A2.3.3.� Does not have performance equivalent (defined by form, fit and function) to those of an article or service used for civil applications; or
���������� AP1.A2.3.4.� Is specifically designed, developed,
configured, adapted, or modified for a military application, and has
significant military or intelligence applicability such that control under this
subchapter is necessary.
AP1.A2.4.� Intended Use:� The intended use of the article or service after its export
(i.e., for a military or civilian purpose) is not relevant in determining
whether the article or service is subject to the controls of this
subchapter.� Any item covered by the
U.S. Munitions List must be within the categories of the U.S. Munitions
List.� The scope of the U.S. Munitions
List shall be changed only by amendments made pursuant to section 38 of the
Arms Export Control Act (22 U.S.C. 2778).
AP1.A2.5.� Determining Jurisdiction
State vs. Commerce� (Commodity
Jurisdiction).
The commodity jurisdiction procedure is used with the U.S.
Government if doubt exists as to whether an article or service is covered by
the U.S. Munitions List.� It may also be
used for consideration of a redesignation of an article or service currently
covered by the U.S. Munitions List.� The
Department must submit a report to Congress at least 30 days before any item is
removed from the U.S. Munitions List.�
Upon written request, the Office of Defense Trade Controls shall provide
a determination of whether a particular article or service is covered by the
U.S. Munitions List.� The determination,
consistent with ITAR par. A120.2, 120.3, and 120.4, entails consultation among
the Departments of State, Defense, Commerce and other U.S. Government agencies
and industry in appropriate cases.
���������� AP1.A2.5.1.� Requests shall identify the article or service, and include a history of the product's design, development and use.� Brochures, specifications and any other documentation related to the article or service shall be submitted in seven collated sets.
���������� AP1.A2.5.2.� The Department of State, shall make a determination that an article or service does not have predominant civil applications in accordance on a case-by-case basis, taking into account:
AP1.A2.5.2.1.� The number, variety and predominance of civil applications;
AP1.A2.5.2.2.� The nature, function and capability of the civil applications; and the nature, function and capability of the military applications.
Note: The form of the item is its defined configuration, including the geometrically measured configuration, density, and weight or other visual parameters, which characterize the item, component or assembly.� For software, form denotes language, language level and media.� The fit of the item is its ability to physically interface or interconnect with or become an integral part of another item. The function of the item is the action or actions it is designed to perform.
���������� AP1.A2.5.3.� A determination that an article has significant military or intelligence applications such that it is necessary to control its export as a defense article shall be made, on a case-by-case basis, taking into account:
AP1.A2.5.3.1.� The nature, function, and capability of the article
AP1.A2.5.3.2.� The nature of controls imposed by other nations on such items (including Wassannar and other multilateral controls), and
AP1.A2.5.3.3.� That items described on the Wassannar Industrial List shall not be designated defense articles or defense services unless the failure to control such items on the U.S.� Munitions List would jeopardize significant national security or foreign policy interests.
AP1.A2.6.� Other Agencies:
���������� AP1.A2.6.1.� The Treasury Department controls permanent imports of articles and services covered by the U.S. Munitions Import List from foreign countries by persons subject to U.S. jurisdiction (31 CFR part 505).�
���������� AP1.A2.6.2.� The Department of Commerce regulates the export of items on the Commerce Control List (CCL) under the Export Administration Regulations (15 Code of Federal Regulations CFR parts 768-799).
AP1.A2.7.� Definitions:
���������� AP1.A2.7.1.� Defense article.� Defense article means any item or technical data designated in ITAR �121.1. The policy described in ITAR � 120.3 is applicable to designations of additional items.� This term includes technical data recorded or stored in any physical form, models, mockups or other items that reveal technical data directly relating to items designated in ITAR � 121.1.� It does not include basic marketing information on function or purpose or general system descriptions.
���������� AP1.A2.7.2.� Significant Military Equipment (SME).� �Significant military equipment means articles for which special export controls are warranted because of their capacity for substantial military utility or capability.� Significant military equipment includes:
�������������������� AP1.A2.7.2.1.� Items in the ITAR �121.1 of which are preceded by an asterisk; and
�������������������� AP1.A2.7.2.2..� All classified articles enumerated in the ITAR �121.1.
���������� AP1.A2.7.3.� Major defense equipment. �Major defense equipment means any item of significant military equipment (ITAR �120.7) on the USML having a research and development cost of more than $50,000,000 or a total production cost of more than $200,000,000.
���������� AP1.A2.7.4.� Defense service. �Defense service means:
�������������������� AP1.A2.7.4.1.� The furnishing of assistance (including training) to foreign persons, whether in the United States or abroad in the design, development, engineering, manufacture, production, assembly, testing, repair, maintenance, modification, operation, demilitarization, destruction, processing or use of defense articles.
�������������������� AP1.A2.7.4.2.� The furnishing to foreign persons of any technical data controlled under ITAR �120.10, whether in the United States or abroad; Military training of foreign units and forces, regular and irregular, including formal or informal instruction of foreign persons in the United States or abroad or by correspondence courses, technical, educational, or information publications and media of all kinds, training aid, orientation, training exercise, and military advice. (See ITAR �124.1.)
���������� AP1.A2.7.5.� Technical data. �Technical data means, information, other than software as defined in the ITAR �120.10(4), which is required for the design, development, production, manufacture, assembly, operation, repair, testing, maintenance or modification of defense articles.� This includes information in the form of blueprints, drawings, photographs, plans, instructions and documentation.
�������������������� AP1.A2.7.5.1.� Classified information relating to defense articles and defense services.
�������������������� AP1.A2.7.5.2� Information covered by an invention secrecy order.
�������������������� AP1.A2.7.5.3.� Software as defined in ITAR �121.8(f)
directly related to defense articles.
Note:� This definition does not include information concerning general
scientific, mathematical or engineering principles commonly taught in schools,
colleges and universities or information in the public domain as defined in
ITAR �120.11.� It also does not include
basic marketing information on function or purpose or general system
descriptions of defense articles.
���������� AP1.A2.7.6.� Public Domain. �Public domain means information which is published and which is generally accessible or available to the public, through sales at newsstands and bookstores; Through subscriptions which are available without restriction to any individual who desires to obtain or purchase the published information; Through second class mailing privileges granted by the U.S. Government; At libraries open to the public or from which the public can obtain documents; Through patents available at any patent office; Through unlimited distribution at a conference, meeting, seminar, trade show or exhibition, generally accessible to the public, in the United States; Through public release (i.e., unlimited distribution) in any form (e.g., not necessarily in published form) after approval by the cognizant U.S. government department or agency (see also �125.4(b)(13) of this subchapter); Through fundamental research in science and engineering at accredited institutions of higher learning in the U.S. where the resulting information is ordinarily published and shared broadly in the scientific community.� Fundamental research is defined to mean basic and applied research in science and engineering where the resulting information is ordinarily published and shared broadly within the scientific community, as distinguished from research the results of which are restricted for proprietary reasons or specific U.S. Government access and dissemination controls.
����������������������� AP1.A2.7.6.1.� University
research will not be considered fundamental research if the University or
its researchers accept other restrictions on publication of scientific and
technical information resulting from the project or activity or the U.S.
Government funds the research and specific access and dissemination controls
protecting information resulting from the research are applicable.
���������� AP1.A2.7.7. �U.S. Person:� U.S.
person means a person (as defined in ITAR section 120.14) who is lawful
permanent resident as defined by 8 U.S.C. 1101(a)(20) or who is a protected
individual as defined by 8 U.S.C. 1324b(a)(3).�
It also means any corporation, business association, partnership,
society, trust, or any other entity, organization or group that is incorporated
to do business in the United States.� It
also includes any governmental (federal, state or local) entity.� It does not include any foreign person as
defined in ITAR section 120.16.
���������� AP1.A2.7.8.� Foreign Person:� Foreign persons means any natural person who is not a lawful permanent resident as defined by 8 U.S.C. 1101(a)(20) or who is not a protected individual as defined by 8 U.S.C. 1324b(a)(3).� It also means any foreign corporation, business association, partnership, trust, society or any other entity or group that is not incorporated or organized to do business in the United States, as well as international organizations, foreign governments and any agency or subdivision of foreign governments (e.g. diplomatic missions).
���������� AP1.A2.7.9.� Export:� Export means:
����������������������� AP1.A2.7.9.1.� Sending or taking a defense article out of the United States in any manner, except by mere travel outside of the United States by a person whose personal knowledge includes technical data.
����������������������� AP1.A2.7.9.2. �Transferring registration, control or ownership to a foreign person of any aircraft, vessel, or satellite covered by the U.S. Munitions List, whether in the United States or abroad.
����������������������� AP1.A2.7.9.3.� Disclosing (including oral or visual disclosure) or transferring in the United States any defense article to an embassy, any agency or subdivision of a foreign government (e.g., diplomatic missions).
����������������������� AP1.A2.7.9.4.� Disclosing (including oral or visual disclosure) or transferring technical data to a foreign person, whether in the United States or abroad.
����������������������� AP1.A2.7.9.5.� Performing a defense service on behalf of,
or for the benefit of, a foreign person, whether in the United States or
abroad.
���������� AP1.A2.7.10.� Temporary import:� Temporary import means bringing into the United States from a foreign country any defense article that is to be returned to the country from which it was shipped or taken, or any defense article that is in transit to another foreign destination.� Temporary import includes withdrawal of a defense article from a customs bonded warehouse or foreign trade zone for the purpose of returning it to the country of origin or country from which it was shipped or for shipment to another foreign destination.� The Department of the Treasury (see 27 CFR parts 47, 178 and 179) regulates permanent imports.
���������� AP1.A2.7.11. �License: �License means a document bearing the word license issued by the Director, Office of Defense Trade Controls or his authorized designee which permits the export or temporary import of a specific defense article or defense service controlled by this subchapter.
���������� AP1.A2.7.12. �Manufacturing license agreement:� An agreement (e.g., contract) whereby a U.S. person grants a foreign person an authorization to manufacture defense articles abroad and which involves or contemplates:
����������������������� AP1.A2.7.12.1.� The export of technical data (as defined in ITAR �120.10) or defense articles or the performance of a defense service.
����������������������� AP1.A2.7.12.2. The use by the foreign person of technical data or defense articles previously exported by the U.S. person. (See ITAR part 124).
���������� AP1.A2.7.13.� Technical
Assistance Agreement (TAA): An agreement for the performance of a defense
service(s) or the disclosure of technical data, as opposed to an agreement
granting a right or license to manufacture defense articles.� Assembly of defense articles is included
under this section, provided production rights or manufacturing know-how are
not conveyed.
���������� AP1.A2.7.14.� Distribution agreement:� An agreement (e.g., a contract) to establish a warehouse or distribution point abroad for defense articles exported from the United States for subsequent distribution to entities in an approved sales territory (see ITAR part 124).
���������� AP1.A2.7.15.� Missile Technology Control Regime (MCTR):� MTCR means the policy statement between the United States, the United Kingdom, the Federal Republic of Germany, France, Italy, Canada, and Japan (April 16, 1987), intended to restrict sensitive missile-relevant transfers based on the MTCR Annex.� The term MTCR Annex means the Guidelines and Equipment and Technology Annex of the MTCR.� The MTCR Annex. Section 71(a) of the Arms Export Control Act (22 U.S.C. �2797) refers to the establishment as part of the U.S. Munitions List of a list of all items on the MTCR Annex, the export of which is not controlled under section 6(l) of the Export Administration Act of 1979 (50 U.S.C. app. 2405(l)).� In accordance with this provision, the list of MTCR Annex items shall constitute all items on the U.S. Munitions List.
���������� AP1.A2.7.16.� U.S. Criminal Statutes (ITAR Part 120.27):� U.S. criminal statutes means:
����������������������� AP1.A2.7.16.1.� Section 38 of the Arms Export Control Act (22 U.S.C. 2778).
����������������������� AP1.A2.7.16.2.� Section 11 of the Export Administration Act of 1979 (50 U.S.C. app. 2410).
����������������������� AP1.A2.7.16.3.� Sections 793, 794, or 798 of title 18, United States Code (relating to espionage involving defense or classified information).
����������������������� AP1.A2.7.16.4.� Section 16 of the Trading with the Enemy Act (50 U.S.C. app. 16).
����������������������� AP1.A2.7.16.5.� Section 206, of the International Emergency Economic Powers Act (relating to foreign assets controls; 50 U.S.C. 1705)
����������������������� AP1.A2.7.16.6.� Section 30A of the Securities Exchange Act of 1934 (15 U.S.C. 78dd-1) or section 104 of the Foreign Corrupt Practices Act (15 U.S.C. 78dd-2).
����������������������� AP1.A2.7.16.7.� Chapter 105 of title 18, United States Code (relating to sabotage).
����������������������� AP1.A2.7.16.8.� Section 4(b) of the Internal Security Act of 1950 (relating to communication of classified information; 50 U.S.C. 783(b)).
����������������������� AP1.A2.7.16.9.� Sections 57, 92, 101, 104, 222, 224, 225, or 226 of the Atomic Energy Act of 1954 (42 U.S.C. 2077, 2122, 2131, 2134, 2272, 2274, 2275, and 2276).
����������������������� AP1.A2.7.16.10.� Section 601 of the National Security Act of 1947 (relating to intelligence identities protection; 50 U.S.C. 421).
����������������������� AP1.A2.7.16.11.� Section 603(b) or (c) of the Comprehensive Anti-Apartheid Act of 1986 (22 U.S.C. 5113(b) and (c)); and
����������������������� AP1.A2.7.l6.12.� Section 371 of title 18, United States Code
